350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.

What does the number 15 represent in this configuration?
Which two components do southbound APIs use to communicate with downstream devices? (Choose two.)
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint
Protection Platform?
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The
company needs to be able to protect sensitive data throughout the full environment. Which tool should be used
to accomplish this goal?
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users,
data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity
platform. What should be used to meet these requirements?
What are two benefits of using Cisco Duo as an MFA solution? (Choose two.)
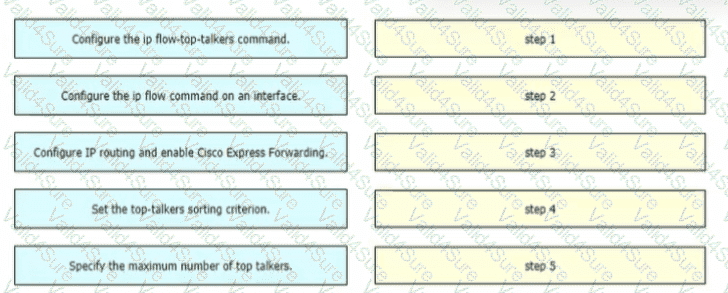
A network engineer is configuring NetFlow top talkers on a Cisco router Drag and drop the steps in the process from the left into the sequence on the right