350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Drag and drop the security solutions from the left onto the benefits they provide on the right.
Which function is performed by certificate authorities but is a limitation of registration authorities?
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.) The eDirectory client must be installed on each client workstation.
II
An engineer musà set up 200 new laptops on a network and wants to prevent the users from moving their laptops around to simplify administration Which switch port MAC address security setting must be used?
Which two commands are required when configuring a flow-export action on a Cisco ASA? (Choose two.)
An organization recently installed a Cisco Secure Web Appliance and would like to take advantage of the AVC engine to allow the organization to create a policy to control application-specific activity. After enabling the AVC engine, what must be done to implement this?
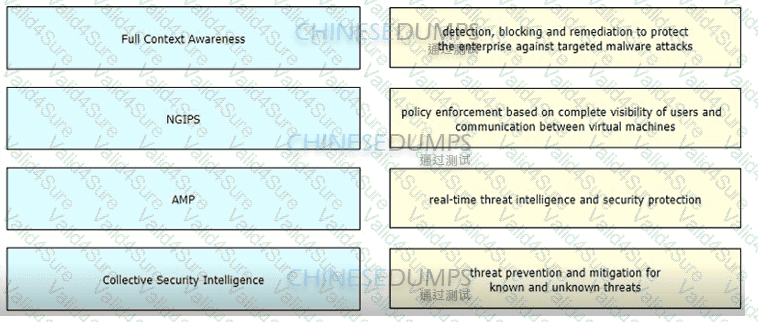
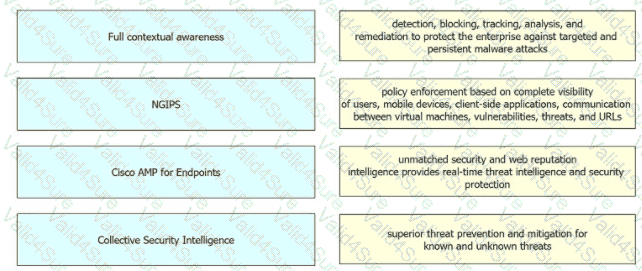
Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right.