350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which technology provides the benefit of Layer 3 through Layer 7 innovative deep packet inspection,
enabling the platform to identify and output various applications within the network traffic flows?
Which type of dashboard does Cisco DNA Center provide for complete control of the network?
What is the term for having information about threats and threat actors that helps mitigate harmful events that would otherwise compromise networks or systems?
Refer to the exhibit.
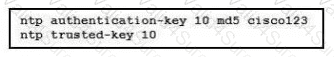
A network engineer is testing NTP authentication and realizes that any device synchronizes time with this router and that NTP authentication is not enforced What is the cause of this issue?