350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
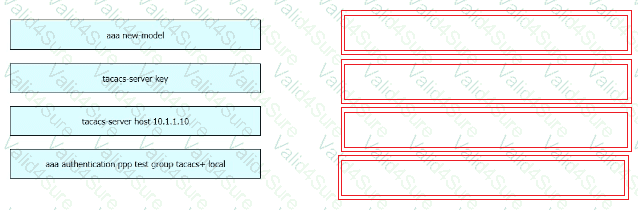
Refer to the exhibit.

An engineer must configure a Cisco switch to perform PPP authentication via a TACACS server located at IP address 10.1.1.10. Authentication must fall back to the local database using the username LocalUser and password C1Sc0451069341l if the TACACS server is unreachable.
Drag and drop the commands from the left onto the corresponding configuration steps on the right.
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two)
A network engineer must configure a Cisco Secure Email Gateway to prompt users to enter two forms of information before gaining access. The Secure Email Gateway must also join a cluster machine using preshared keys. What must be configured to meet these requirements?
Which Cisco firewall solution supports configuration via Cisco Policy Language?
What is the purpose of the certificate signing request when adding a new certificate for a server?
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?