350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
With Cisco AMP for Endpoints, which option shows a list of all files that have been executed in your
environment?
Which DoS attack uses fragmented packets in an attempt to crash a target machine?
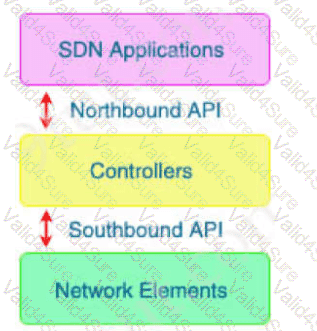
With which components does a southbound API within a software-defined network architecture communicate?
A network administrator is configuring SNMPv3 on a new router. The users have already been created;
however, an additional configuration is needed to facilitate access to the SNMP views. What must the
administrator do to accomplish this?
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443. The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users. What must be done on the Cisco WSA to support these requirements?
Which Cisco cloud security software centrally manages policies on multiple platforms such as Cisco ASA, Cisco Firepower, Cisco Meraki, and AWS?