350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
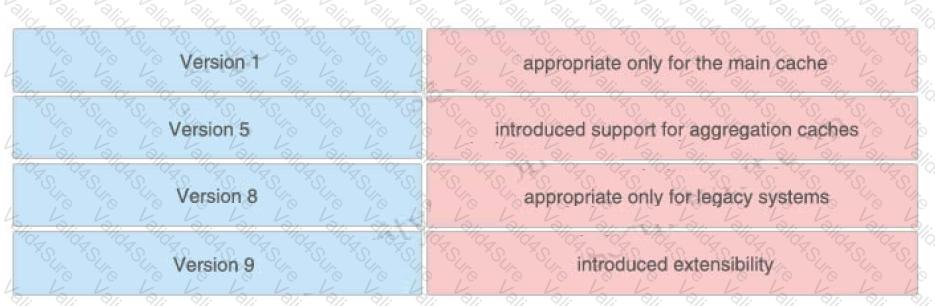
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
Refer to the exhibit.

A network administrator configures command authorization for the admin5 user. What is the admin5 user able to do on HQ_Router after this configuration?
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline
posture node?
A networking team must harden an organization's network from VLAN hopping attacks. The team disables Dynamic Trunking Protocol and puts any unused ports in an unused VLAN. A trunk port is used as a trunk link. What must the team configure next to harden the network against VLAN hopping attacks?
An engineer is deploying Cisco Advanced Malware Protection (AMP) for Endpoints and wants to create a policy that prevents users from executing file named abc424952615.exe without quarantining that file What type of Outbreak Control list must the SHA.-256 hash value for the file be added to in order to accomplish this?
