350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A company has 5000 Windows users on its campus. Which two precautions should IT take to prevent WannaCry ransomware from spreading to all clients? (Choose two.)
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with
other cloud solutions via an API. Which solution should be used to accomplish this goal?
Which characteristic is unique to a Cisco WSAv as compared to a physical appliance?
When NetFlow is applied to an interface, which component creates the flow monitor cache that is used
to collect traffic based on the key and nonkey fields in the configured record?
Which security solution uses NetFlow to provide visibility across the network, data center, branch
offices, and cloud?
An engineer is configuring Cisco Umbrella and has an identity that references two different policies. Which action ensures that the policy that the identity must use takes precedence over the second one?
An organization has a Cisco ESA set up with policies and would like to customize the action assigned for
violations. The organization wants a copy of the message to be delivered with a message added to flag it as a
DLP violation. Which actions must be performed in order to provide this capability?
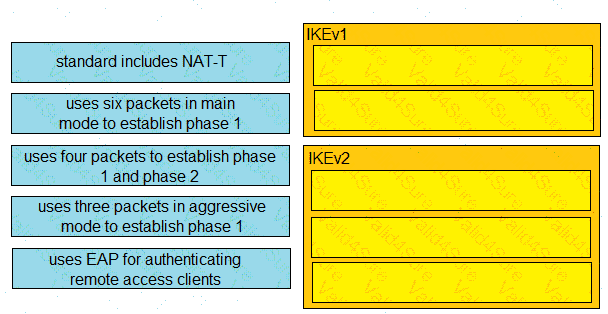
Drag and drop the descriptions from the left onto the correct protocol versions on the right.