CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
Searching for workable clues to ace the CompTIA CAS-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CAS-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
During an incident response activity, the response team collected some artifacts from a compromised server, but the following information is missing:
• Source of the malicious files
• Initial attack vector
• Lateral movement activities
The next step in the playbook is to reconstruct a timeline. Which of the following best supports this effort?
During a security assessment using an CDR solution, a security engineer generates the following report about the assets in me system:
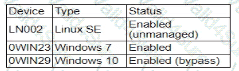
After five days, the EDR console reports an infection on the host 0WIN23 by a remote access Trojan Which of the following is the most probable cause of the infection?
An organization purchased a new manufacturing facility and the security administrator needs to:
• Implement security monitoring.
• Protect any non-traditional device(s)/network(s).
• Ensure no downtime for critical systems.
Which of the following strategies best meets these requirements?
A company wants to install a three-tier approach to separate the web. database, and application servers A security administrator must harden the environment which of the following is the best solution?
A security architect is performing threat-modeling activities related to an acquired overseas software company that will be integrated with existing products and systems Once its software is integrated, the software company will process customer data for the acqumng company Given the following:
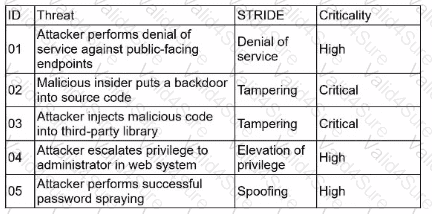
Which of the following mitigations would reduce the risk of the most significant threats?