CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
Searching for workable clues to ace the CompTIA CAS-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CAS-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A security analyst is performing threat modeling for a new AI chatbot. The AI chatbot will be rolled out to help customers develop configuration information within the company's SaaS offering. Which of the following issues would require involvement from the company's internal legal team?
A company detects suspicious activity associated with inbound connections. Security detection tools are unable to categorize this activity. Which of the following is the best solution to help the company overcome this challenge?
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:
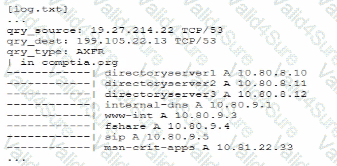
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A company wants to implement hardware security key authentication for accessing sensitive information systems The goal is to prevent unauthorized users from gaining access with a stolen password Which of the following models should the company implement to b«st solve this issue?
A security architect must make sure that the least number of services as possible is exposed in order to limit an adversary's ability to access the systems. Which of the following should the architect do first?
A global company’s Chief Financial Officer (CFO) receives a phone call from someone claiming to be the Chief Executive Officer (CEO). The caller claims to be stranded and in desperate need of money. The CFO is suspicious, but the caller’s voice sounds similar to the CEO’s. Which of the following best describes this type of attack?
An organization recently implemented a new email DLP solution. Emails sent from company email addresses to matching personal email addresses generated a large number of alerts, but the content of the emails did not include company data. The security team needs to reduce the number of emails sent without blocking all emails to common personal email services. Which of the following should the security team implement first?
An organization would like to increase the effectiveness of its incident response process across its multiplatform environment. A security engineer needs to implement the improvements using the organization's existing incident response tools. Which of the following should the security engineer use?