CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
Searching for workable clues to ace the CompTIA CAS-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CAS-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
During the course of normal SOC operations, three anomalous events occurred and were flagged as potential IoCs. Evidence for each of these potential IoCs is provided.
INSTRUCTIONS
Review each of the events and select the appropriate analysis and remediation options for each IoC.
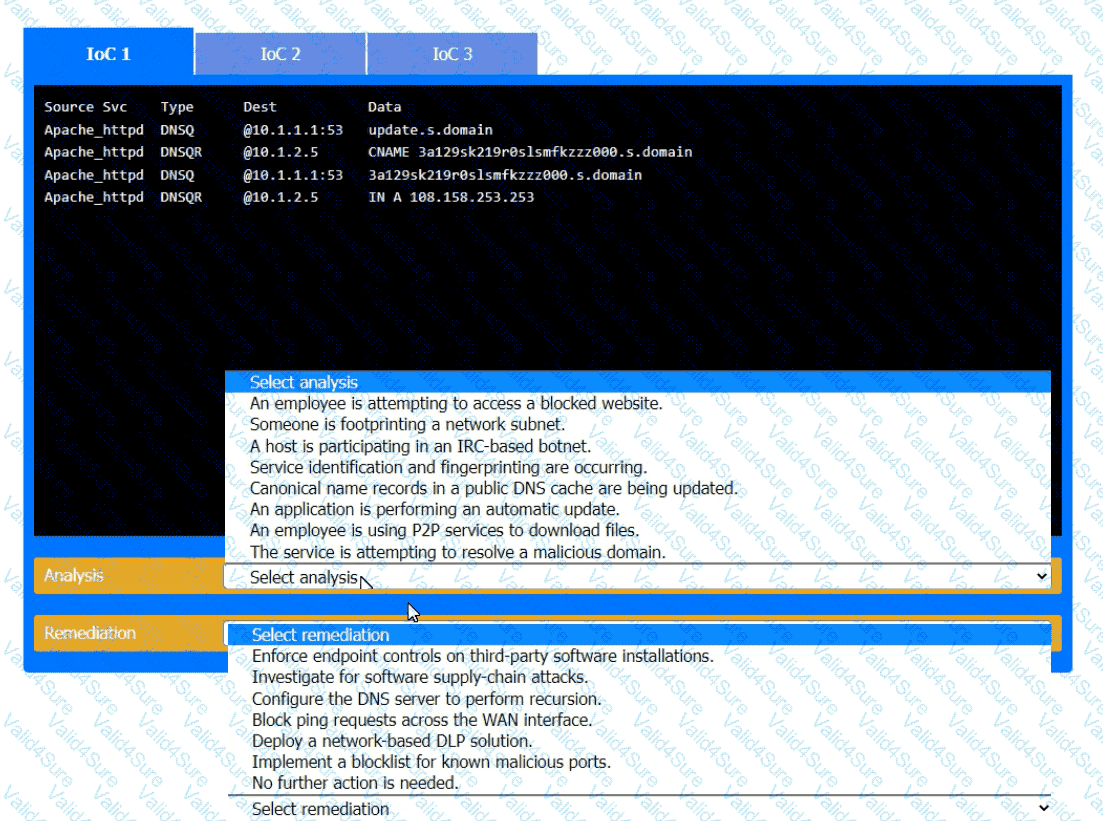
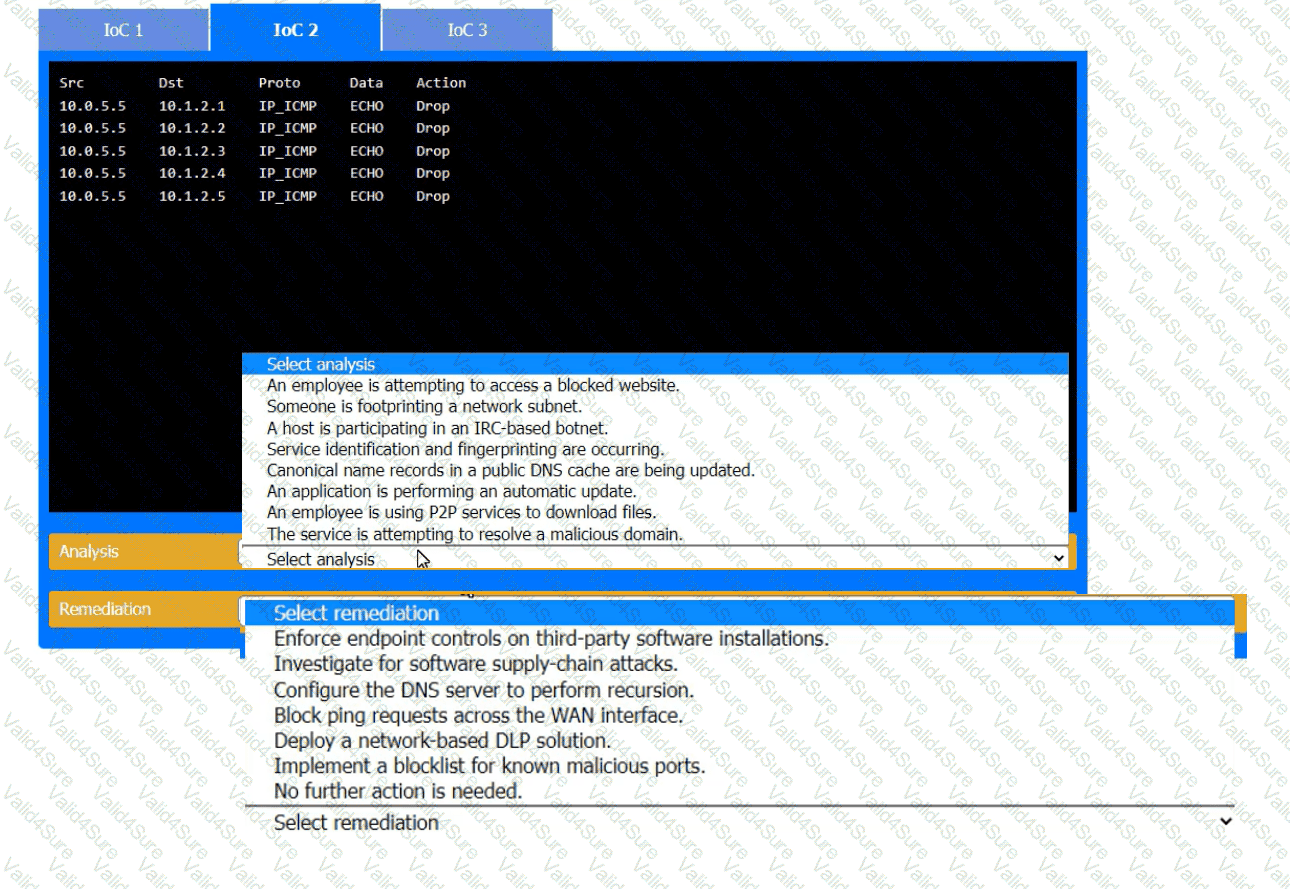
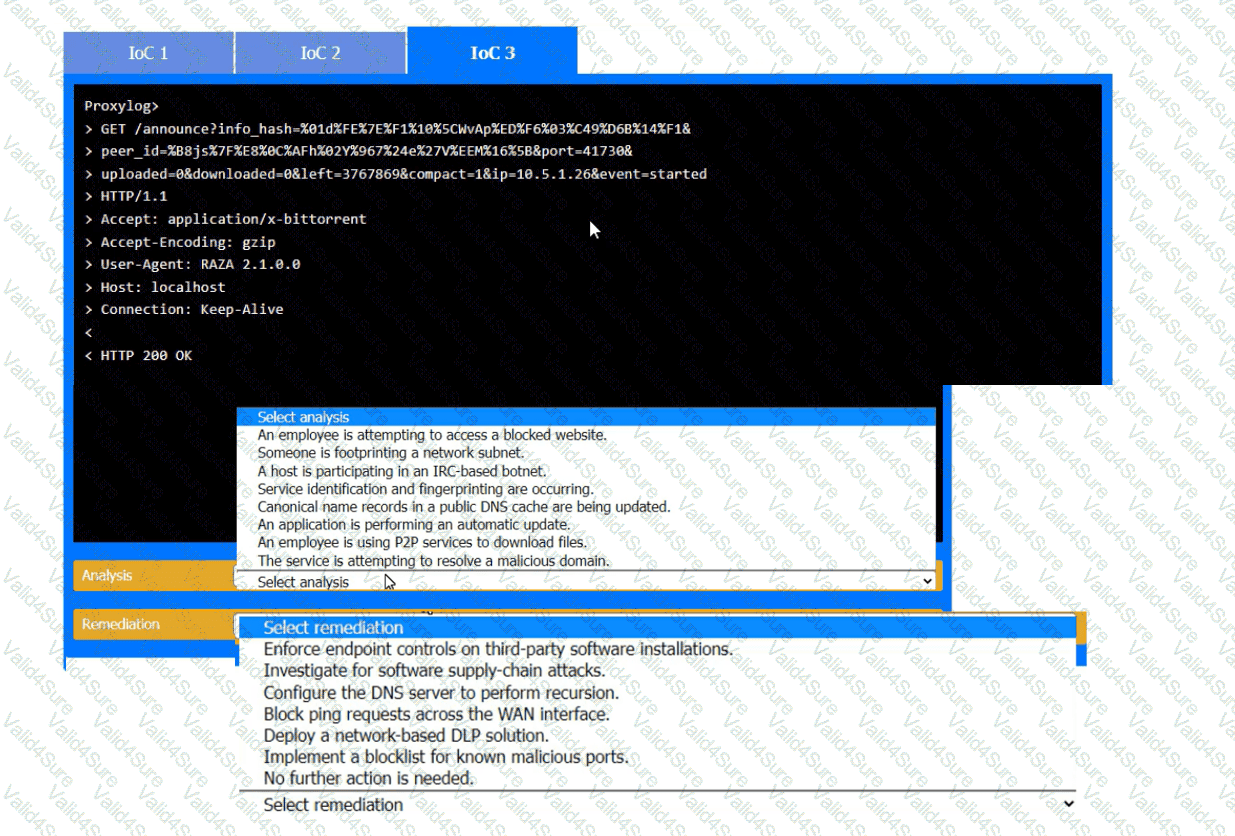
The device event logs sourced from MDM software are as follows:
Device | Date/Time | Location | Event | Description
ANDROID_102 | 01JAN21 0255 | 38.9072N, 77.0369W | PUSH | APPLICATION 1220 INSTALL QUEUED
ANDROID_102 | 01JAN21 0301 | 38.9072N, 77.0369W | INVENTORY | APPLICATION 1220 ADDED
ANDROID_1022 | 01JAN21 0701 | 39.0067N, 77.4291W | CHECK-IN | NORMAL
ANDROID_1022 | 01JAN21 0701 | 25.2854N, 51.5310E | CHECK-IN | NORMAL
ANDROID_1022 | 01JAN21 0900 | 39.0067N, 77.4291W | CHECK-IN | NORMAL
ANDROID_1022 | 01JAN21 1030 | 39.0067N, 77.4291W | STATUS | LOCAL STORAGE REPORTING 85% FULL
Which of the following security concerns and response actions would best address the risks posed by the device in the logs?
A company sells a security appliance assembled from globally sourced hardware and software components. Installing the security appliance requires enabling administrative permissions for the service accounts on the appliance. Which of the following allows the company to reassure new and existing customers that the risk introduced by the appliance is minimal?
Anorganization has noticed an increase in phishing campaigns utilizingtyposquatting. A security analyst needs to enrich the data for commonly used domains against the domains used in phishing campaigns. The analyst uses a log forwarder to forward network logs to the SIEM. Which of the following would allow the security analyst to perform this analysis?
The ISAC for the retail industry recently released a report regarding social engineering tactics in which small groups create distractions for employees while other malicious individuals install advanced card skimmers on the payment systems. The Chief Information Security Officer (CISO) thinks that security awareness training, technical control implementations, and governance already in place is adequate to protect from this threat. The board would like to test these controls. Which of the following should the CISO recommend?
A security engineer wants to stay up-to-date on new detections that are released on a regular basis. The engineer's organization uses multiple tools rather than one specific vendor security stack. Which of the following rule-based languages is the most appropriate to use as a baseline for detection rules with the multiple security tool setup?
A user reports application access issues to the help desk. The help desk reviews the logs for the user:
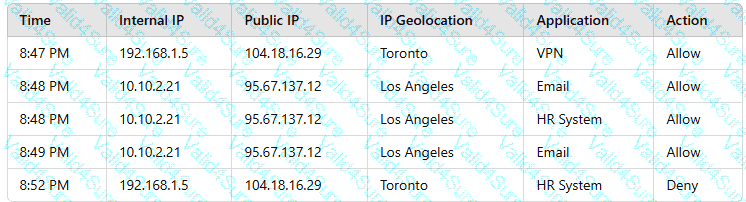
Which of the following is most likely the reason for the issue?
A security analyst Detected unusual network traffic related to program updating processes The analyst collected artifacts from compromised user workstations. The discovered artifacts were binary files with the same name as existing, valid binaries but. with different hashes which of the following solutions would most likely prevent this situation from reoccurring?