CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
Searching for workable clues to ace the CompTIA CAS-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CAS-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
An organization recently hired a third party to audit the information security controls present in the environment. After reviewing the audit findings, the Chief Information Security Officer (CISO) approved the budget for an in-depth defense strategy for network security. Which of the following is the most likely reason the CISO approved the additional budget?
A security engineer is reviewing the following vulnerability scan report:
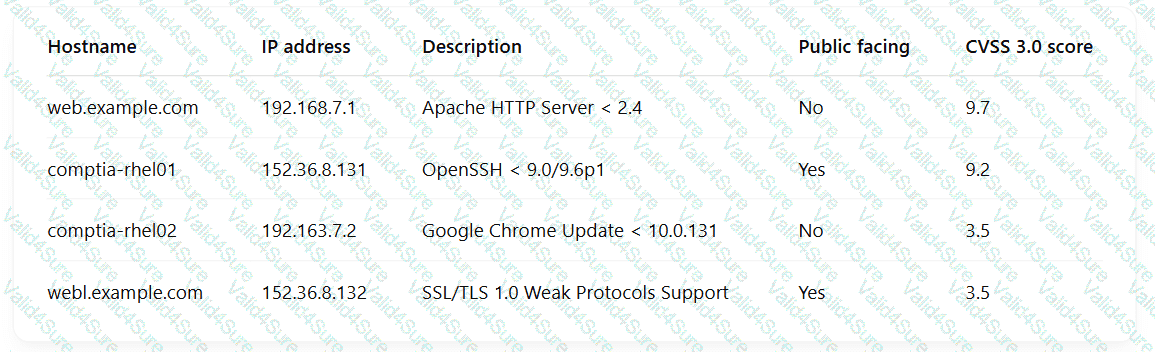
Which of the following should the engineer prioritize for remediation?
A security engineer receives an alert from the SIEM platform indicating a possible malicious action on the internal network. The engineer generates a report that outputs the logs associated with the incident:

Which of the following actions best enables the engineer to investigate further?
A software development team requires valid data for internal tests. Company regulations, however do not allow the use of this data in cleartext. Which of the following solutions best meet these requirements?
A security engineer wants to improve the security of an application as part of the development pipeline. The engineer reviews the following component of an internally developed web application that allows employees to manipulate documents from a number of internal servers:
response = requests.get(url)
Users can specify the document to be parsed by passing the document URL to the application as a parameter. Which of the following is the best solution?
A central bank implements strict risk mitigations for the hardware supply chain, including an allow list for specific countries of origin. Which of the following best describes the cyberthreat to the bank?
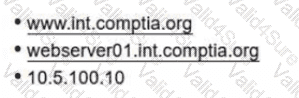
An administrator needs to craft a single certificate-signing request for a web-server certificate. The server should be able to use the following identities to mutually authenticate other resources over TLS:
• wwwJnt.comptia.org
• webserver01.int.comptia.org
•10.5.100.10
Which of the following certificate fields must be set properly to support this objective?
Which of the following supports the process of collecting a large pool of behavioral observations to inform decision-making?