CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
Searching for workable clues to ace the CompTIA CAS-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CAS-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function:
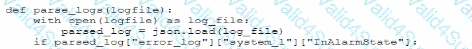
Which of the following is most likely the log input that the code will parse?
A)
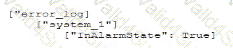
B)

C)
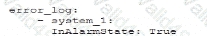
D)
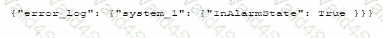
An organization is implementing Zero Trust architecture A systems administrator must increase the effectiveness of the organization's context-aware access system. Which of the following is the best way to improve the effectiveness of the system?
During a recentsecurity event, access from thenon-production environment to the production environmentenabledunauthorized usersto:
Installunapproved software
Makeunplanned configuration changes
During theinvestigation, the following findings were identified:
Several new users were added in bulkby theIAM team
Additionalfirewalls and routerswere recently added
Vulnerability assessmentshave been disabled formore than 30 days
Theapplication allow listhas not been modified intwo weeks
Logs were unavailablefor various types of traffic
Endpoints have not been patchedinover ten days
Which of the following actions would most likely need to be taken toensure proper monitoring?(Select two)
A threat intelligence company's business objective is to allow customers to integrate data directly to different TIPs through an API. The company would like to address as many of the following objectives as possible:
• Reduce compute spend as much as possible.
• Ensure availability for all users.
• Reduce the potential attack surface.
• Ensure the integrity of the data provided.
Which of the following should the company consider to best meet the objectives?
A company is preparing to move a new version of a web application to production. No issues were reported during security scanning or quality assurance in the CI/CD pipeline. Which of the following actions should thecompany take next?
Source code snippets for two separate malware samples are shown below:
Sample 1:
knockEmDown(String e) {
if(target.isAccessed()) {
target.toShell(e);
System.out.printIn(e.toString());
c2.sendTelemetry(target.hostname.toString + " is " + e.toString());
} else {
target.close();
}
}
Sample 2:
targetSys(address a) {
if(address.islpv4()) {
address.connect(1337);
address.keepAlive("paranoid");
String status = knockEmDown(address.current);
remote.sendC2(address.current + " is " + status);
} else {
throw Exception e;
}
}
Which of the following describes the most important observation about the two samples?
A security analyst needs to ensure email domains that send phishing attempts without previous communications are not delivered to mailboxes The following email headers are being reviewed
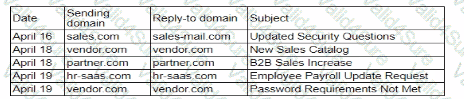
Which of thefollowing is the best action for the security analyst to take?
After a penetration test on the internal network, the following report was generated:
Attack Target Result
Compromised host ADMIN01S.CORP.LOCAL Successful
Hash collected KRBTGT.CORP.LOCAL Successful
Hash collected SQLSV.CORP.LOCAL Successful
Pass the hash SQLSV.CORP.LOCAL Failed
Domain control CORP.LOCAL Successful
Which of the following should be recommended to remediate the attack?