CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
Searching for workable clues to ace the CompTIA CAS-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CAS-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following best describes the reason a network architect would enable forward secrecy on all VPN tunnels?
A SOC analyst is investigating an event in which a penetration tester was able to successfully create and execute a payload. The analyst pulls the following command history from the affected server-
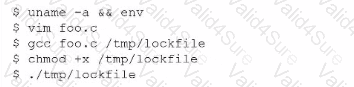
Which of the following should the analyst implement lo improve the security of the server?
A security engineer receives the following findings from a recent security audit:
• Data should be protected based on user permissions and roles.
• User action tracking should be implemented across the network.
• Digital identities should be validated across the data access workflow.
Which of the following is the first action the engineer should take to address the findings?
A systems administrator wants to use existing resources to automate reporting from disparate security appliances that do not currently communicate. Which of the following is the best way to meet this objective?
The identity and access management team is sending logs to the SIEM for continuous monitoring. The deployed log collector isforwarding logs to
the SIEM. However, only false positive alerts are being generated. Which of the following is the most likely reason for the inaccurate alerts?
A systems administrator works with engineers to process and address vulnerabilities as a result of continuous scanning activities. The primary challenge faced by the administrator is differentiating between valid and invalid findings. Which of the following would the systems administrator most likely verify is properly configured?
A cybersecurity architect is reviewing the detection and monitoring capabilities for a global company that recently made multiple acquisitions. The architect discovers that the acquired companies use different vendors for detection and monitoring The architect's goal is to:
• Create a collection of use cases to help detect known threats
• Include those use cases in a centralized library for use across all of the companies
Which of the following is the best way to achieve this goal?
An organization hires a security consultant to establish a SOC that includes athreat-modeling function. During initial activities, the consultant works with system engineers to identify antipatterns within the environment. Which of the following is most critical for the engineers to disclose to the consultant during this phase?