The question addresses the selection of a project methodology for a small organization delivering network design services, a key aspect of the CCDE v3.1 blueprint under "Business-Driven Design Approaches." The requirements emphasize visualization of progress, iterative feedback incorporation, and flexibility to adapt scope without significantly disrupting the project outcome. The CCDE v3.1 blueprint highlights the importance of aligning project management methodologies with business objectives, ensuring that network design projects meet customer needs while maintaining agility and efficiency.
Analysis of Requirements:
Visualization of Project Scope and Weekly Progress:Management needs a clear, real-time view of the project’s status, including tasks completed, in progress, and planned. This requires a methodology with tools for visual tracking, such as boards or dashboards.
Feedback Incorporation and Iterative Changes:The methodology must support continuous feedback from stakeholders (e.g., customers or management) and allow for adjustments to the design throughout the project lifecycle.
Flexibility to Change Scope:The ability to modify the project scope (e.g., adding or removing network design components) at any time without derailing the project is critical.
Least Impact on Project Outcome:The methodology should minimize disruptions to the project’s success (e.g., timeline, quality, or deliverables) when changes are made.
Analysis of Options:
A. Scrum:Scrum is an Agile framework that organizes work into fixed-length iterations (sprints), typically 2–4 weeks. It uses visual tools like sprint backlogs and burndown charts to track progress, meeting the visualization requirement. Scrum incorporates feedback at the end of each sprint during sprint reviews, allowing for iterative changes. However, scope changes within a sprint are discouraged, as Scrum prioritizes completing the sprint backlog. Changing the scope mid-sprint can disrupt the team’s focus and impact the outcome (e.g., incomplete deliverables or delayed timelines). While Scrum supports flexibility between sprints, it’s less ideal for mid-iteration scope changes, making it suboptimal for the requirement of changing scope at any point.
B. Lean:Lean focuses on maximizing value by eliminating waste and optimizing processes. It emphasizes continuous improvement and customer value but doesn’t inherently provide a structured framework for visualizing project progress or managing iterative feedback in the context of network design projects. Lean’s focus on streamlining processes is less suited for handling frequent scope changes, as it prioritizes efficiency over flexibility. Additionally, Lean lacks specific tools like visual boards tailored to project management, making it less effective for meeting the visualization requirement. Its impact on the outcome could be significant if scope changes disrupt optimized workflows.
C. Kanban:Kanban is a visual, flow-based methodology that uses a Kanban board to track tasks in columns (e.g., To Do, In Progress, Done), providing real-time visualization of project scope and progress. It supports continuous feedback by allowing teams to adjust priorities and incorporate changes as new tasks are added to the board. Kanban’s strength is its flexibility: tasks can be reprioritized, and scope changes can be introduced at any time without disrupting the workflow, as there are no fixed iterations. Work-in-progress (WIP) limits ensure that the team remains focused, minimizing the impact of changes on the project outcome. Kanban’s adaptability and minimal structure make it ideal for a small team delivering network design services with evolving requirements, aligning perfectly with all three requirements and ensuring the least impact on the outcome.
D. Six Sigma:Six Sigma is a data-driven methodology focused on reducing defects and improving quality through structured processes (e.g., DMAIC: Define, Measure, Analyze, Improve, Control). It’s designed for process optimization, not project management, and lacks tools for visualizing project progress or supporting iterative feedback in a network design context. Six Sigma’s rigid, phased approach doesn’t accommodate frequent scope changes, as changes could require restarting the DMAIC cycle, significantly impacting the project outcome. It’s unsuitable for the dynamic, flexible needs of this project.
Correct Answer (C):
Kanbanis the best methodology to meet the requirements:
Visualization:Kanban boards provide a clear, real-time view of tasks and progress, accessible to management.
Feedback and Iterative Changes:Kanban supports continuous feedback by allowing tasks to be updated or reprioritized based on stakeholder input.
Flexibility for Scope Changes:New tasks can be added, and priorities can shift at any time without disrupting the workflow, as Kanban operates without fixed iterations.
Least Impact on Outcome:Kanban’s flow-based approach and WIP limits ensure that changes are absorbed smoothly, maintaining project stability and deliverables.
Why Not A, B, or D?
Scrum (A):While Scrum supports visualization and feedback, its fixed sprints limit flexibility for mid-iteration scope changes, potentially impacting the outcome if changes are frequent.
Lean (B):Lean lacks specific project management tools for visualization and is less suited for handling scope changes, as it prioritizes process efficiency over flexibility.
Six Sigma (D):Six Sigma is designed for quality control, not project management, and its rigid structure doesn’t support visualization, feedback, or scope flexibility.
Relevant CCDE v3.1 Blueprint Extract:
The CCDE v3.1 blueprint, as outlined in theCisco Certified Design Expert (CCDE 400-007) Official Cert Guideand Cisco Learning Network resources, includes the following under "Business-Driven Design Approaches":
Project Management Methodologies:Selecting methodologies that align with business requirements, such as Agile, Lean, or Kanban, to deliver network design projects effectively.
Customer-Centric Design:Incorporating stakeholder feedback and adapting to changing requirements to meet business objectives.
Agility and Flexibility:Designing processes that allow for iterative improvements and scope adjustments without compromising project outcomes.
FromCisco Certified Design Expert (CCDE 400-007) Official Cert Guide(2023):
"Business-driven design requires project methodologies that support flexibility and stakeholder collaboration. Kanban is particularly effective for projects with evolving requirements, as its visual workflow and continuous delivery model allow for real-time adjustments with minimal disruption."
FromCCDE v3 Practice Labs: Preparing for the Cisco Certified Design Expert Lab Exam(Duggan, 2023):
"For small teams delivering network design services, Kanban provides a lightweight, flexible approach. Its visual board supports management oversight, while its flow-based structure accommodates scope changes without impacting project stability."
Industry-Standard Reference:
Kanban is widely recognized in project management literature (e.g.,Kanban: Successful Evolutionary Change for Your Technology Businessby David J. Anderson) as a methodology that excels in dynamic environments. It’s particularly suited for small teams, as it requires minimal overhead and supports continuous delivery, aligning with Cisco’s emphasis on business-driven, agile design processes.
Official Cisco Documentation Reference:
Cisco’s CCDE training materials and the Cisco Learning Network emphasize Agile methodologies for network design projects, with Kanban highlighted for its ability to manage workflows in environments with frequent changes. TheCisco Enterprise Architecturemodel encourages modular, iterative approaches to align with business needs, which Kanban supports through its flexible structure.
Sources:
Cisco Certified Design Expert (CCDE 400-007) Official Cert Guide, Cisco Press, 2023.
CCDE v3 Practice Labs: Preparing for the Cisco Certified Design Expert Lab Exam, Martin J. Duggan, Cisco Press, 2023.
Cisco Learning Network, CCDE v3.1 Blueprint and Resources.
Kanban: Successful Evolutionary Change for Your Technology Business, David J. Anderson, 2010 (for Kanban methodology principles).
CCDE Study Guide, Cisco Press, 2015 (for foundational business-driven design concepts, updated by CCDE v3.1 materials).
Conclusion:
The correct answer isC (Kanban), as it fully meets the requirements for visualization, feedback incorporation, and scope flexibility while minimizing impact on the project outcome. Kanban’s visual, flow-based approach is ideal for a small organization delivering network design services with dynamic requirements, aligning with the CCDE v3.1 blueprint’s focus on business-driven design approaches.
Notes on Corrections and Process:
Typographical Errors Corrected:
Minor formatting adjustments for clarity (e.g., consistent bullet points for requirements).
Changed “out-come†to “outcome†in the question stem.
Ensured consistent capitalization for methodology names (e.g., “Six Sigma†instead of “Six-Sigmaâ€).
Verification Process:
Cross-referenced the question with the CCDE v3.1 blueprint from the Cisco Learning Network and Cisco Press resources (CCDE 400-007 Official Cert GuideandCCDE v3 Practice Labs).
Validated Kanban’s suitability using industry-standard project management principles and Cisco’s guidance on Agile methodologies.
Ensured the explanation aligns with CCDE v3.1’s emphasis on business-driven, customer-centric design processes.
Answer Selection:
SelectedCbased on Kanban’s direct alignment with all requirements, ruling out other options through detailed comparison of their suitability for the scenario.
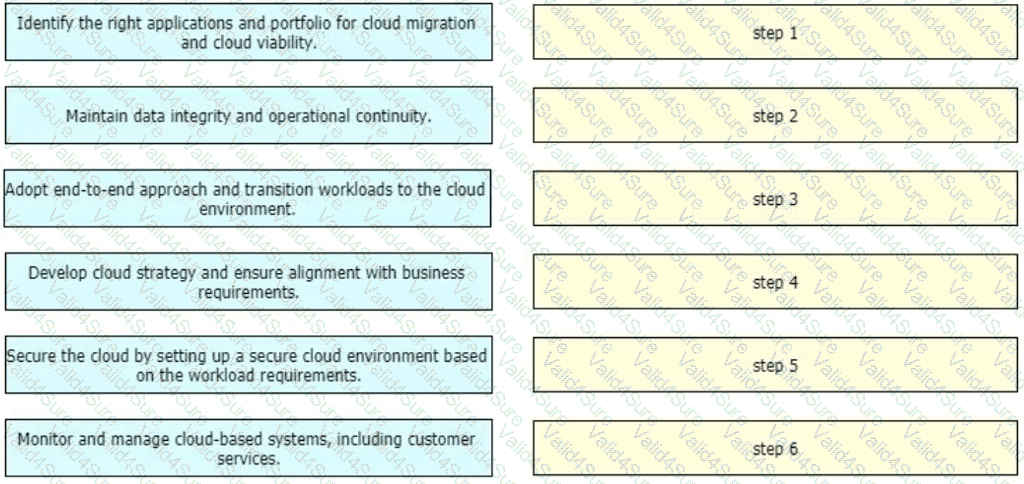
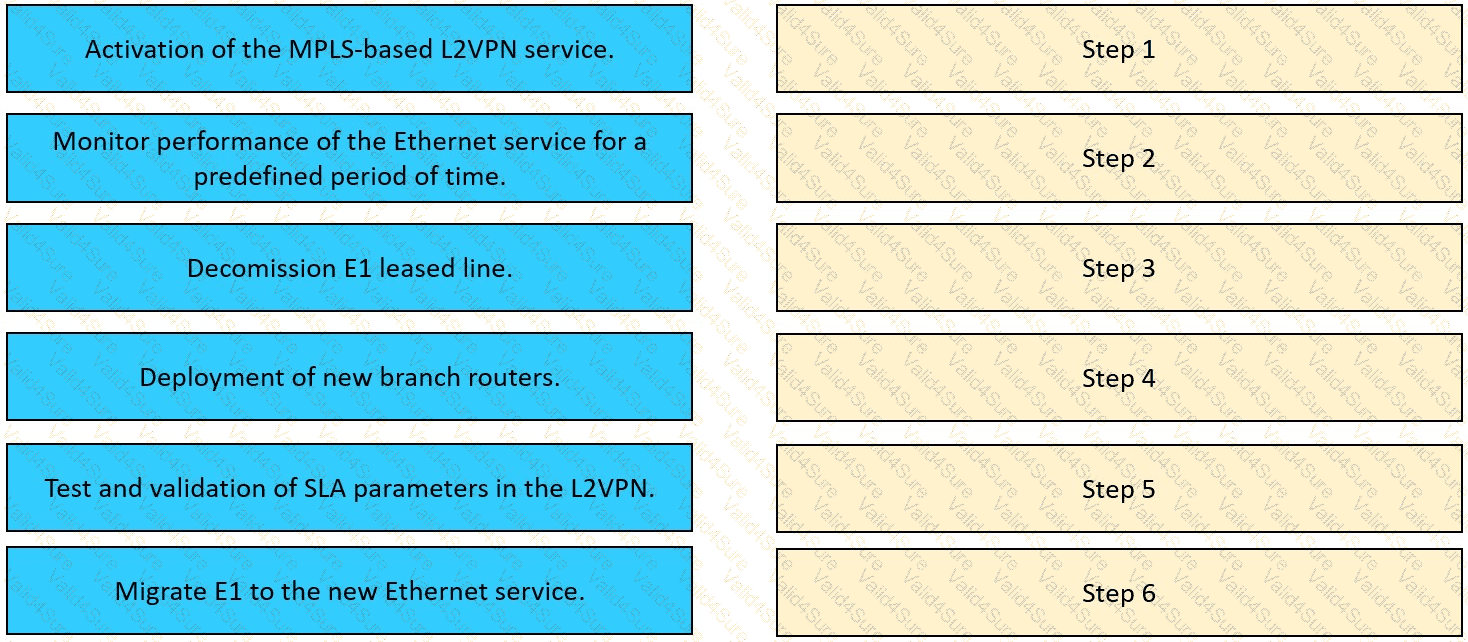
 Table
Description automatically generated
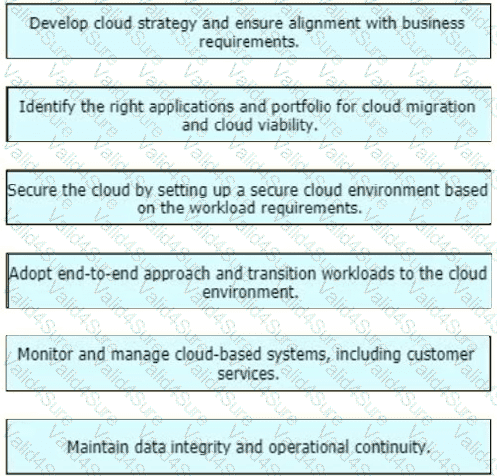
Table
Description automatically generated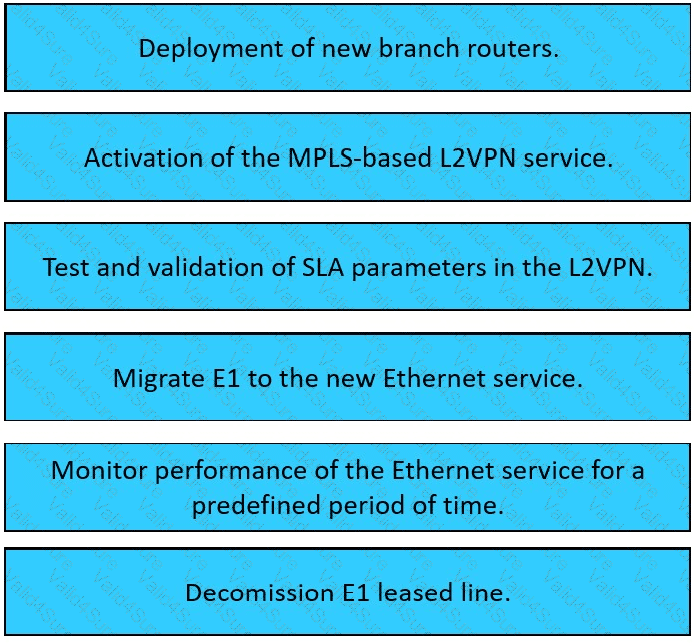 Table
Description automatically generated
Table
Description automatically generated