400-007 Exam Dumps - Cisco Certified Design Expert (CCDE v3.1)
Searching for workable clues to ace the Cisco 400-007 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 400-007 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
What is a country-specific requirement that data is subject to the laws of the country in which it is collected or processed and must remain within its borders?
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. They want to extend the existing IP CCTV network to a new branch without routing changes or IP address changes. What is the best approach?
Which two features are advantages of SD-WAN compared to MPLS-based connectivity? (Choose two.)
Refer to the exhibit.
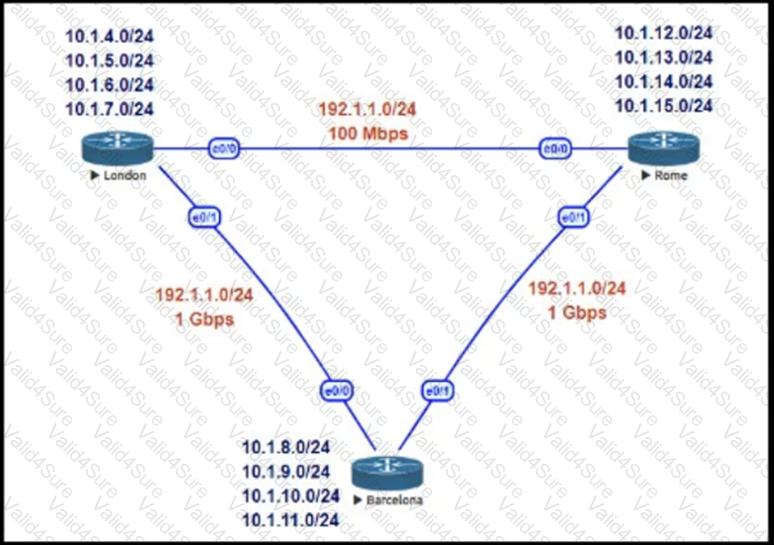
This network is running EIGRP as the routing protocol and the internal networks are being advertised in EIGRP. Based on the link speeds, all traffic between London and Rome is getting propagated via Barcelona and the direct link between London and Rome is not being utilized under normal working circumstances. The EIGRP design should allow for efficiency in the routing table by minimizing the routes being exchanged. The link between London and Rome should be utilized for specific routes. Which two steps accomplish this task? (Choose two.)
A software-defined network exposes an API to the RIB and forwarding engine, allowing off-box control of routing—what SDN model is used?
A business wants to refresh its legacy Frame Relay WAN and consolidate product specialists via video in 200 branches. Which technology should be used?