400-007 Exam Dumps - Cisco Certified Design Expert (CCDE v3.1)
Searching for workable clues to ace the Cisco 400-007 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 400-007 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A company requires an RPO of less than 10 seconds to ensure business continuity. Which technology should be deployed?
A BGP route reflector in the network is taking longer than expected to converge during large network changes. Troubleshooting shows that the router cannot handle all the TCP acknowledgements during route updates. Which action can be performed to tune the device performance?
Company XYZ, a global content provider, owns data centers on different continents. Their data center design involves a standard three-layer design with a Layer 3-only core. VRRP is used as the FHRP. They require VLAN extension across access switches in all data centers and plan to purchase a Layer 2 interconnection between two of their data centers in Europe. In the absence of other business or technical constraints, which termination point is optimal for the Layer 2 interconnection?
An enterprise plans to evolve from a traditional WAN network to a software-defined WAN network. The existing devices have limited capability when it comes to virtualization. As the migration is carried out, enterprise applications and services must not experience any traffic impact. Which implementation plan can be used to accommodate this during the migration phase?
A European government passport agency considers upgrading its IT systems to increase performance and workload flexibility in response to constantly changing requirements. The budget manager wants to reduce capital expenses and IT staff and must adopt the lowest-cost technology. Which technology choice is suitable?
Sometimes SDN leverages various overlay networking technologies to create layer(s) of network abstraction. What describes an overlay network?
Refer to the exhibit.
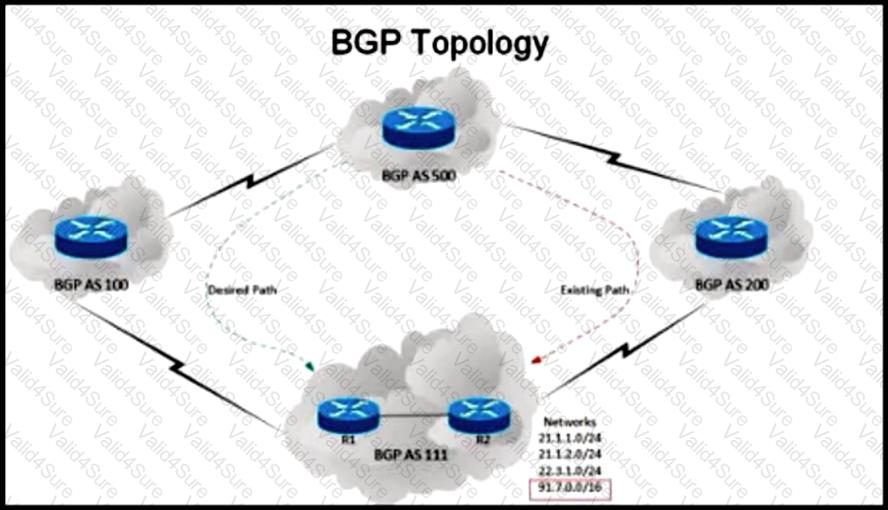
An engineer has been asked to redesign the traffic flow toward AS 111 coming from AS 500. Traffic destined to AS 111 network 91.7.0.0/16 should come in via AS 100, while traffic destined to all other networks in AS 111 should continue to use the existing path. Which BGP attributes are best suited to control this inbound traffic coming from BGP AS 500 into the 91.7.0.0/16 network?
Company XYZ wants to secure the data plane of their network. Which two technologies can be included in the security design? (Choose two)