350-501 Exam Dumps - Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR)
Searching for workable clues to ace the Cisco 350-501 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-501 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.
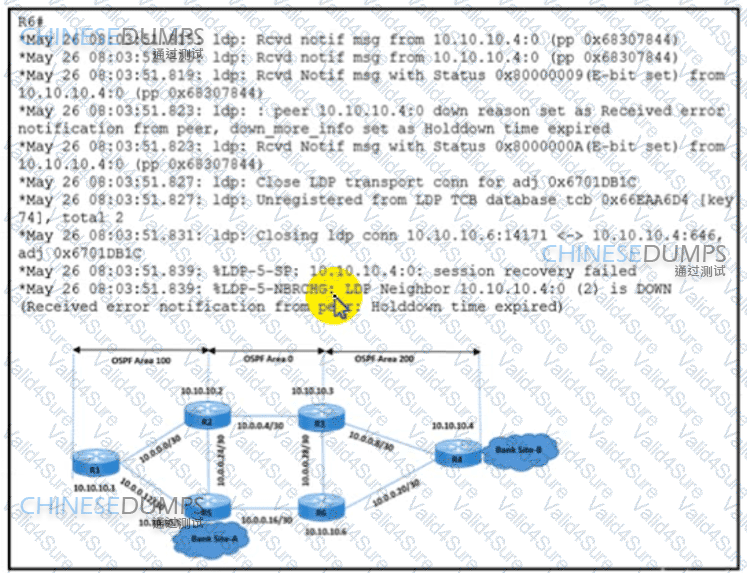
A network engineer is implementing an LDP-based MPLS solution to enable packet flow between the two bank sites The engineer was given two requirements
·LDP peering must stay up when there is a link failure between R3 and R6
·LDP peering must not flap when there is a link failure between R5 and R6
Which action meets these requirements?
Refer to the exhibit:
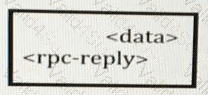
This output is included at the end of an output that was provided by a device using NETCONF.
What does the code show?
Refer to the exhibit.
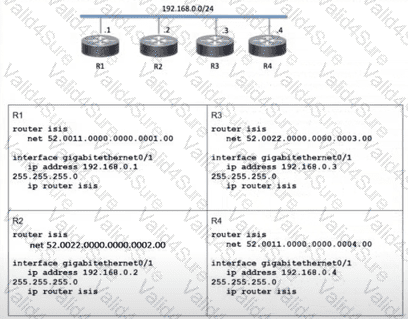
Which two topology changes happen to the IS-IS routers? (Choose two.)
A regional company is planning to bolster the security of their LAN infrastructure by implementing advanced encryption techniques between their core switch and their distribution switch. The solution must leverage hardware-accelerated encryption capabilities to transparently encrypt all traffic between the two switches at the data-link layer to safeguard against unauthorized access. However, it is important for the solution to have minimal impact on network performance and latency.
Which action must the engineer take to meet the requirements?
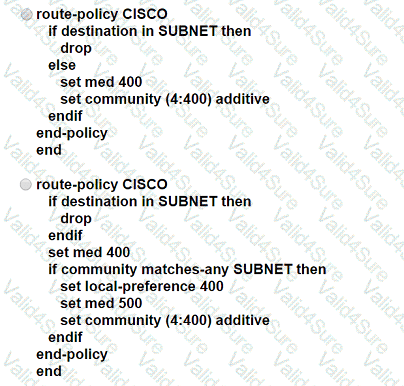
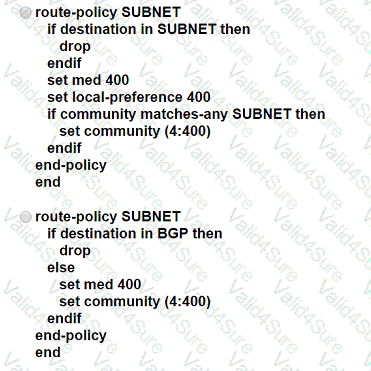
A network engineer is configuring a BGP route policy for the SUBNET prefix set. Matching traffic must be dropped, and other traffic must have its MED value set to 400 and community 4:400 added to the route. Which configuration must an engineer apply?

Refer to the exhibit. The network team must implement MPLS LDP session protection with two requirements:
Session protection is provided for core loopback IP addresses only.
The LDP session must remain operational for one hour when the WAN link on PE-XR1 fails.
Which configuration must the team implement on PE-XR1?