350-501 Exam Dumps - Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR)
Searching for workable clues to ace the Cisco 350-501 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-501 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit:
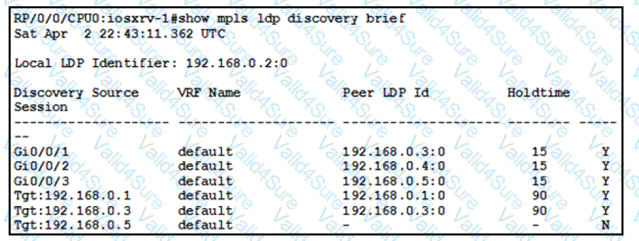
With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?
An engineer must implement QoS to prioritize traffic that requires better service throughout the network. The engineer started by configuring a class map to identify the high-priority traffic. Which additional tasks must the engineer perform to implement the new QoS policy?
A network engineer must implement an ACL-based solution to mitigate availability issues on a web service that is hosted on a server at IP address 172.16.15.18/23. Access to the web server should be allowed over HTTP from RFC 1918 addresses only. The network architect has already enabled PMTUD in the network. Which ACL configuration must the engineer implement to complete the task?