350-401 Exam Dumps - Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
Searching for workable clues to ace the Cisco 350-401 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-401 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which feature allows clients to perform Layer 2 roaming between wireless controllers?
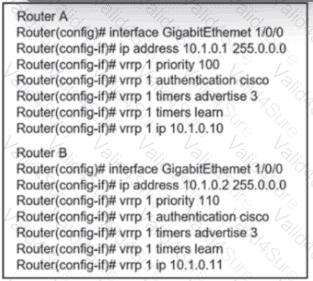
Refer to the exhibit. An engineer must adjust the configuration so that Router A becomes the active router. Which commands should be applied to router A? (Choose two)
Which language defines the structure or modelling of data for NETCONF and RESTCONF?
Which DNS record type is needed to allow a Cisco AP to discover a WLC when using IPv4?
Which feature provides data-plane security for Cisco Catalyst SD-WAN networks'?
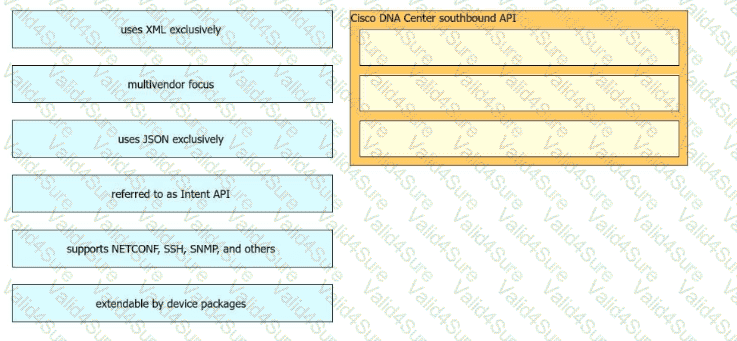
Drag and drop the Cisco Catalyst Center (formerly DNA Center) southbound API characteristics from the left to the right. Not all options are used.
What is used by vManage to interact withCiscoSD-WAN devices in the fabric?
Which type of tunnel is required between two WLCs to enable intercontroller roaming?