350-401 Exam Dumps - Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
Searching for workable clues to ace the Cisco 350-401 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-401 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps

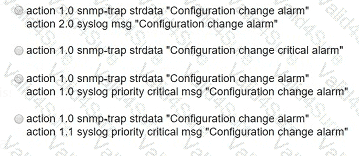
Refer to the exhibit. A network engineer must be notified when a user switches to configuration mode. Which script should be applied to receive an SNMP trap and a critical-level log message?
Which characteristic applies to the endpoint security aspect of the Cisco Threat Defense architecture?
What is one characteristic of an AP that is operating in Mobility Express mode?
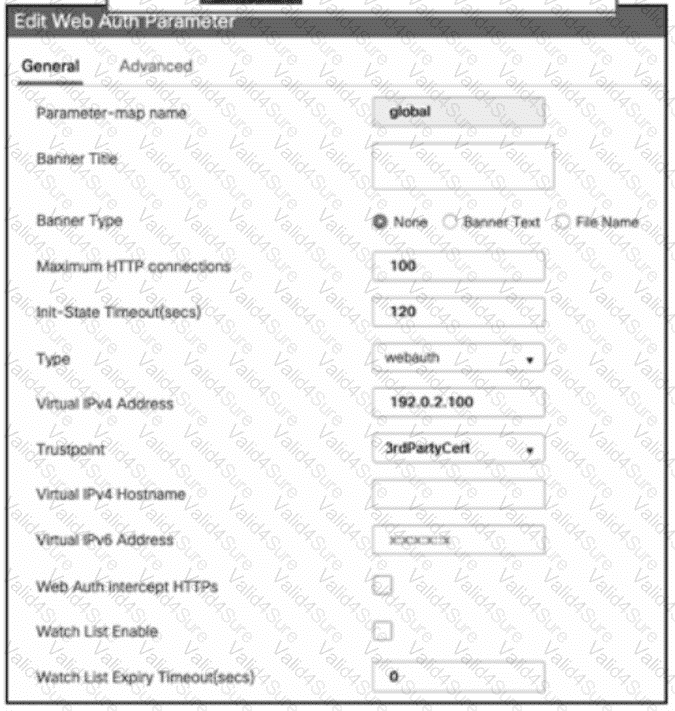
Reler to the exhibit. An engineer configuring WebAuth on a Cisco Catalyst 9000 Series WIC. The engineer has purchased a third-party certificate using the FQDN of the WLC as the CN and intends to use bit on the WebAuth splash page What must be configured so that the clients do not receive a certificate error?
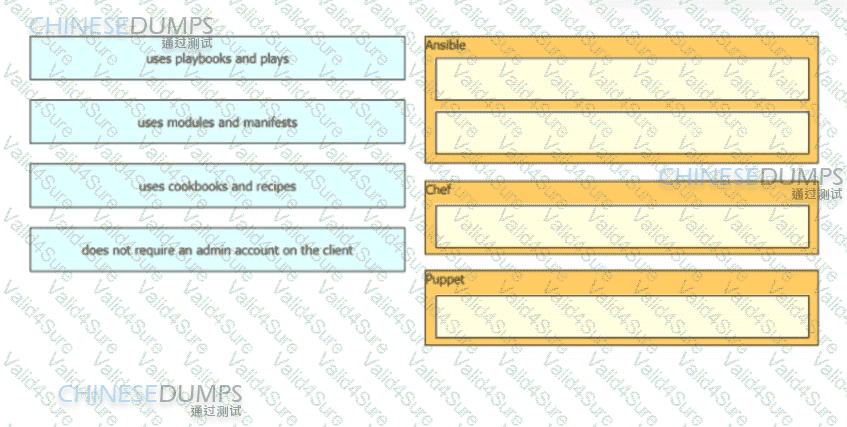
Drag and drop the automation characteristics from the left to the corresponding tools on the right.
Which statement describes the IP and MAC allocation requirements for virtual machines on types 1 hypervisors?