ISO-IEC-27001-Lead-Auditor Exam Dumps - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Searching for workable clues to ace the PECB ISO-IEC-27001-Lead-Auditor Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s ISO-IEC-27001-Lead-Auditor PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Scenario 5: Data Grid Inc. is a well-known company that delivers security services across the entire information technology infrastructure. It provides cybersecurity software, including endpoint security, firewalls, and antivirus software. For two decades, Data Grid Inc. has helped various companies secure their networks through advanced products and services. Having achieved reputation in the information and network security field, Data Grid Inc. decided to obtain the ISO/IEC 27001 certification to better secure its internal and customer assets and gain competitive advantage.
Data Grid Inc. appointed the audit team, who agreed on the terms of the audit mandate. In addition, Data Grid Inc. defined the audit scope, specified the audit criteria, and proposed to close the audit within five days. The audit team rejected Data Grid Inc.'s proposal to conduct the audit within five days, since the company has a large number of employees and complex processes. Data Grid Inc. insisted that they have planned to complete the audit within five days, so both parties agreed upon conducting the audit within the defined duration. The audit team followed a risk-based auditing approach.
To gain an overview of the main business processes and controls, the audit team accessed process descriptions and organizational charts. They were unable to perform a deeper analysis of the IT risks and controls because their access to the IT infrastructure and applications was restricted. However, the audit team stated that the risk that a significant defect could occur to Data Grid Inc.'s ISMS was low since most of the company's processes were automated. They therefore evaluated that the ISMS, as a whole, conforms to the standard requirements by asking the representatives of Data Grid Inc. the following questions:
•How are responsibilities for IT and IT controls defined and assigned?
•How does Data Grid Inc. assess whether the controls have achieved the desired results?
•What controls does Data Grid Inc. have in place to protect the operating environment and data from malicious software?
•Are firewall-related controls implemented?
Data Grid Inc.'s representatives provided sufficient and appropriate evidence to address all these questions.
The audit team leader drafted the audit conclusions and reported them to Data Grid Inc.'s top management. Though Data Grid Inc. was recommended for certification by the auditors, misunderstandings were raised between Data Grid Inc. and the certification body in regards to audit objectives. Data Grid Inc. stated that even though the audit objectives included the identification of areas for potential improvement, the audit team did not provide such information.
Based on this scenario, answer the following question:
Which type of audit risk was defined as “low* by the audit team? Refer to scenario 5.
Question:
An organization is evaluating the materiality of different processes within its ISMS. It is assessing the direct expenses involved with personnel, third-party services, and general fees. Which factor of materiality is the company primarily considering?
Question:
Which of the following statements regarding documented information in an organization's ISMS is incorrect?
Question:
EquiBank is undergoing an external audit of its financial management system. The auditors evaluate the logic of transactions processed by EquiBank's financial software. To ensure accuracy, they use simulations to validate operations, calculations, and controls programmed in the software applications. What type of Computer-Assisted Audit Technique (CAAT) is used?
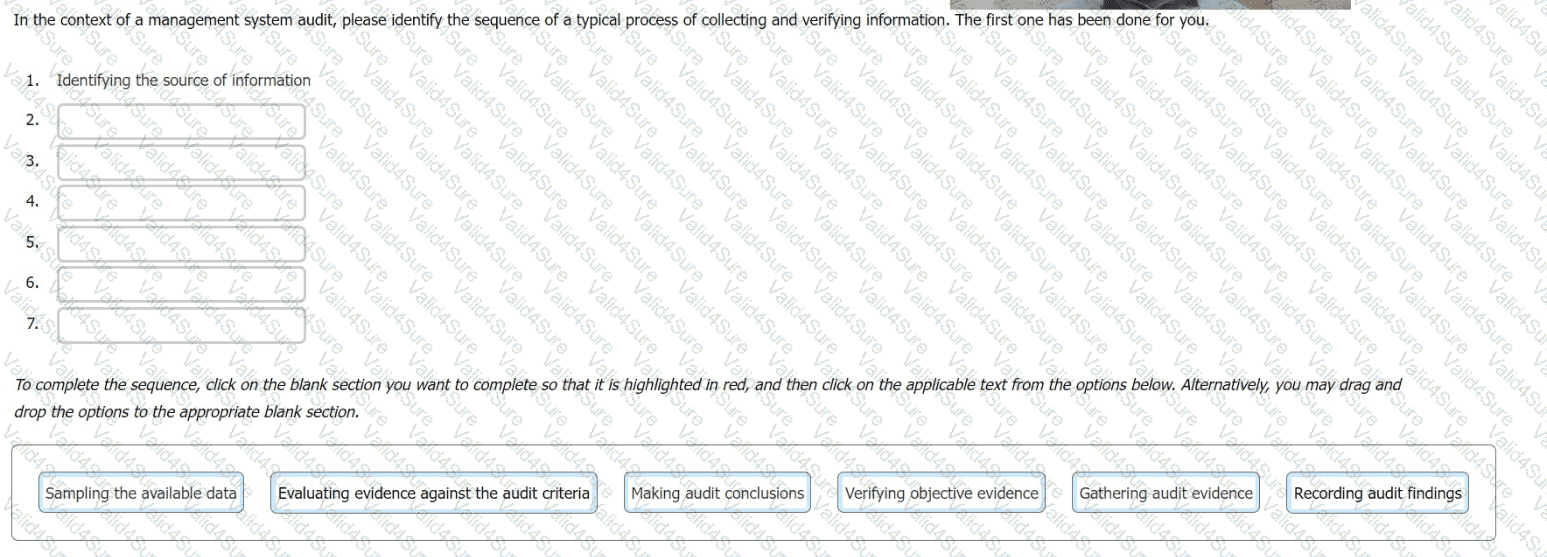
In the context of a management system audit, please identify the sequence of a typical process of collecting and verifying information. The first one has been done for you.