ISO-IEC-27001-Lead-Auditor Exam Dumps - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Searching for workable clues to ace the PECB ISO-IEC-27001-Lead-Auditor Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s ISO-IEC-27001-Lead-Auditor PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
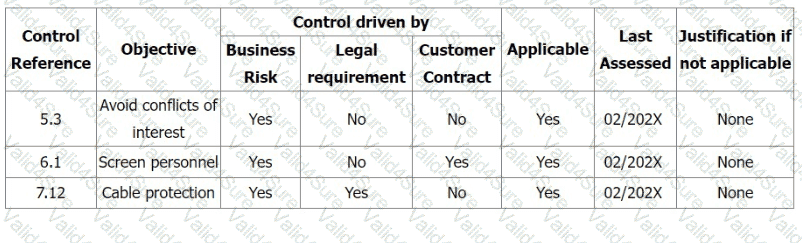
You are the audit team leader conducting a third-party audit of an online insurance organisation. During Stage 1, you found that the organisation took a very cautious risk approach and included all the information security controls in ISO/IEC 27001:2022 Appendix A in their Statement of Applicability.
During the Stage 2 audit, your audit team found that there was no evidence of the implementation of the three controls (5.3 Segregation of duties, 6.1 Screening, 7.12 Cabling security) shown in the extract from the Statement of Applicability. No risk treatment plan was found.
Select three options for the actions you would expect the auditee to take in response to a
nonconformity against clause 6.1.3.e of ISO/IEC 27001:2022.
Which three of the following work documents are not required for audit planning by an auditor conducting a certification audit?
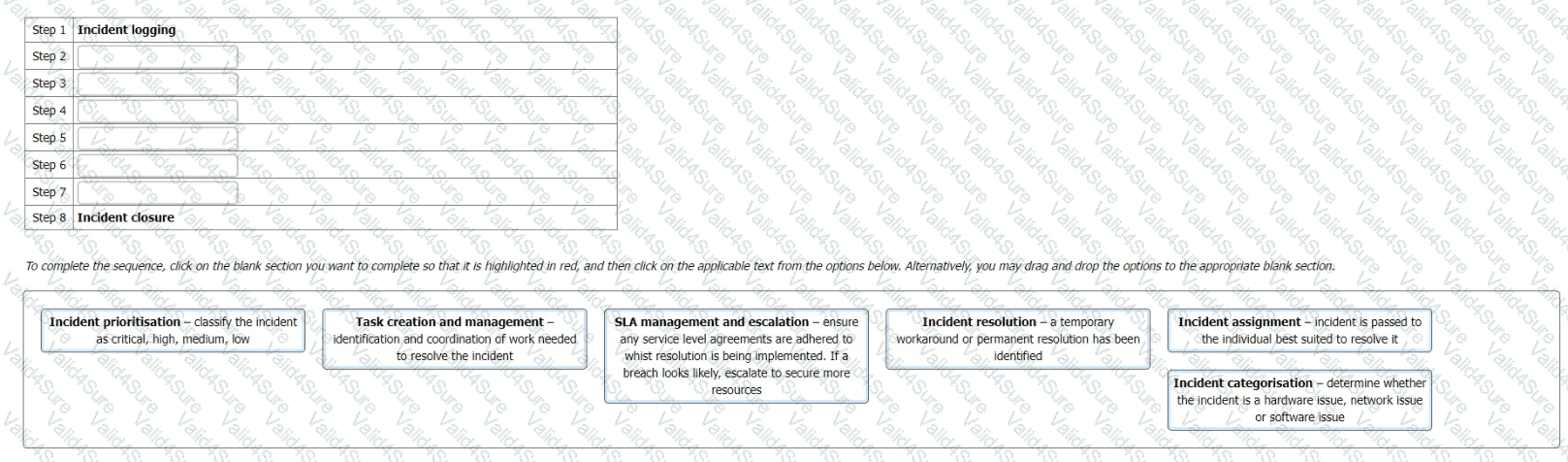
Your organisation is currently seeking ISO/IEC27001:2022 certification. You have just qualified as an Internal ISMS auditor and the ICT Manager wants to use your newly acquired knowledge to assist him with the design of an information security incident management process.
He identifies the following stages in his planned process and asks you to confirm which order they should appear in.
Which one of the following options is the definition of an interested party?
A third party can appeal to an organisation when it perceives itself to be affected by a decision or activity
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security incident management process. The IT Security Manager presents the information security incident management procedure (Document reference ID: ISMS_L2_16, version 4).
You review the document and notice a statement "Any information security weakness, event, and incident should be reported to the Point of Contact (PoC) within 1 hour after identification". When interviewing staff, you found that there were differences in the understanding of the meaning of the phrase "weakness, event, and incident".
The IT Security Manager explained that an online "information security handling" training seminar was conducted 6 months ago. All the people interviewed participated in and passed the reporting exercise and course assessment.
You would like to investigate other areas further to collect more audit evidence. Select three
options that would not be valid audit trails.