ISO-IEC-27001-Lead-Auditor Exam Dumps - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Searching for workable clues to ace the PECB ISO-IEC-27001-Lead-Auditor Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s ISO-IEC-27001-Lead-Auditor PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Scenario 5
CyberShielding Systems Inc. provides security services spanning the entire information technology infrastructure. It provides cybersecurity software, including endpoint security, firewalls, and antivirus software. CyberShielding Systems Inc. has helped various companies secure their networks for two decades through advanced products and services. Having achieved a reputation in the information and network security sector, CyberShielding Systems Inc. decided to implement a security information management system (ISMS) based on ISO/IEC 27001 and obtain a certification to better secure its internal and customer assets and gain a competitive advantage.
The certification body initiated the process by selecting the audit team for CyberShielding Systems Inc.'s ISO/IEC 27001 certification. They provided the company with the name and background information of each audit member. However, upon review, CyberShielding Systems Inc. discovered that one of the auditors did not hold the security clearance required by them. Consequently, the company objected to the appointment of this auditor. Upon review, the certification body replaced the auditor in response to CyberShielding Systems Inc.'s objection.
As part of the audit process, CyberShielding Systems Inc.'s approach to risk and opportunity determination was assessed as a standalone activity. This involved examining the organization’s methods for identifying and managing risks and opportunities. The audit team’s core objectives encompassed providing assurance on the effectiveness of CyberShielding Systems Inc.'s risk and opportunity identification mechanisms and reviewing the organization's strategies for addressing these determined risks and opportunities. During this, the audit team also identified a risk due to a lack of oversight in the firewall configuration review process, where changes were implemented without proper approval, potentially exposing the company to vulnerabilities. This finding highlighted the need for stronger internal controls to prevent such issues.
The audit team accessed process descriptions and organizational charts to understand the main business processes and controls. They performed a limited analysis of the IT risks and controls because their access to the IT infrastructure and applications was limited by third-party service provider restrictions. However, the audit team stated that the risk of a significant defect occurring in CyberShielding’s ISMS was low since most of the company's processes were automated. They therefore evaluated that the ISMS, as a whole, conforms to the standard requirements by questioning CyberShielding representatives on IT responsibilities, control effectiveness, and anti-malware measures. CyberShielding’s representatives provided sufficient and appropriate evidence to address all these questions.
Despite the agreement signed before the audit, which outlined the audit scope, criteria, and objectives, the audit was primarily focused on assessing conformity with established criteria and ensuring compliance with statutory and regulatory requirements.
Question
Was the audit team’s assessment of CyberShielding Systems Inc.'s risk and opportunity determination conducted in accordance with established auditing norms? Refer to Scenario 5.
You are an experienced ISMS auditor conducting a third-party surveillance audit at an organisation which offers ICT reclamation services. ICT equipment which companies no longer require is processed by the organisation. It is either recommissioned and reused or is securely destroyed.
You notice two servers on a bench in the corner of the room. Both have stickers on them with the server's name, IP address and admin password. You ask the ICT Manager about them, and he tells you they were part of a shipment received yesterday from a regular customer.
Which one action should you take?
Which one of the following options describes the main purpose of a Stage 1 audit?
To determine readiness for Stage 2
PayBell, a finance corporation, is using an accounting software to track financial transactions. The software can be accessed from anywhere with an internet connection. It also enables PayBell's employees to easily collaborate with each other to ensure accurate financial reporting. What type of services is PayBell using?
You are an experienced ISMS internal auditor.
You have just completed a scheduled information security audit of your organisation when the IT Manager approaches you and asks for your assistance in the revision of the company's Statement of Applicability.
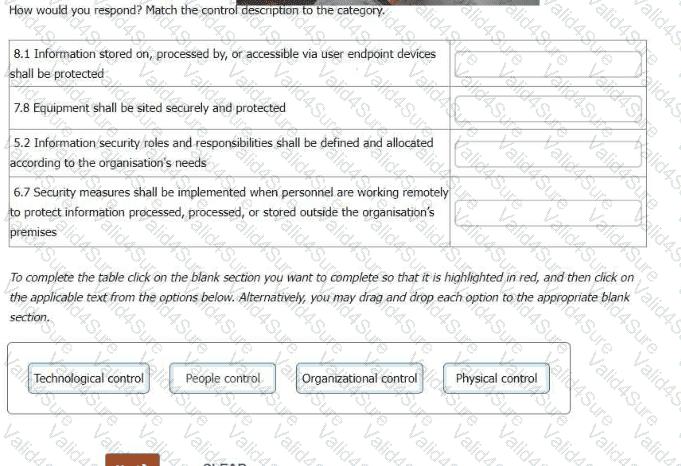
The IT Manager is attempting to update the ISO/IEC 27001:2013 based Statement of Applicability to a Statement aligned to the 4 control themes present in ISO/IEC 27001:2022 (Organizational controls, People Controls, Physical Controls, Technical Controls).
The IT Manager is happy with their reassignment of controls, with the following exceptions. He asks you which of the four control categories each of the following should appear under.
Objectives, criteria, and scope are critical features of a third-party ISMS audit. Which two issues are audit objectives?
Evaluate customer processes and functions