ISO-IEC-27001-Lead-Auditor Exam Dumps - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Searching for workable clues to ace the PECB ISO-IEC-27001-Lead-Auditor Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s ISO-IEC-27001-Lead-Auditor PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
Based on Scenario 6, what methods did the audit team use for evidence collection and analysis during the audit of Sinvestment's ISMS?
Scenario 4
SendPay is a financial services company specializing in global money transfers through a network of agents and institutions. As a new company in the market, SendPay aims to deliver top-quality services with its fee-free digital platform, launched last year, enabling clients to send and receive money anytime via smartphones and laptops. At that time, SendPay outsourced software operations to an external team, which also managed the company's technology infrastructure.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year.
During the audit, the auditors focused on reviewing SendPay’s outsourced operations, specifically looking at the software development and technology infrastructure maintenance handled by the outsourced company. They followed a structured approach, which included reviewing and evaluating SendPay’s processes for monitoring the quality of these outsourced operations. This included verifying if the company met its contractual obligations, ensuring proper governance procedures for engaging outsourced entities, and assessing SendPay’s plans in case of expected or unexpected termination of outsourcing agreements.
However, the auditors subtly noted that SendPay’s protocols did not fully address contingencies for unanticipated cancellations of outsourcing agreements. Additionally, a technical expert appointed by SendPay assisted the auditors, providing specific knowledge and expertise related to the outsourced operations being audited.
The audit team calculated the number of training hours employees received on ISMS to ensure alignment with established objectives. They also computed the average resolution time of information security incidents based on a sample taken during the audit, which provided valuable insights into SendPay’s incident management practices. In addition, the auditors evaluated the reliability of the evidence collected during the audit. They considered several factors influencing the reliability of audit evidence. For example, evidence from surveillance cameras provided more objective proof compared to photos. Timing also played a crucial role in reliability, with mechanisms like transaction recording enhancing the credibility of the evidence.
SendPay uses cloud-based platforms to make its operations more efficient and scalable. However, during the audit, the auditors did not request SendPay to provide an inventory of their cloud activities due to resource limitations, relying instead on SendPay’s representations.
Question
Based on Scenario 4, is the involvement of all the parties acceptable during the auditing of the outsourced operations?
Which two of the following statements are true?
The benefits of implementing an ISMS primarily result from a reduction in information security risks
Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
UpNet outsourced the internal audit function, as provided in scenario 9. Does it impact the internal audit process?
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security incident management process. The IT Security Manager presents the information security incident management procedure and explains that the process is based on ISO/IEC 27035-1:2016.
You review the document and notice a statement "any information security weakness, event, and incident should be reported to the Point of Contact (PoC) within 1 hour after identification". When interviewing staff, you found that there were differences in the understanding of the meaning of "weakness, event, and incident".
You sample incident report records from the event tracking system for the last 6 months with summarized results in the following table.
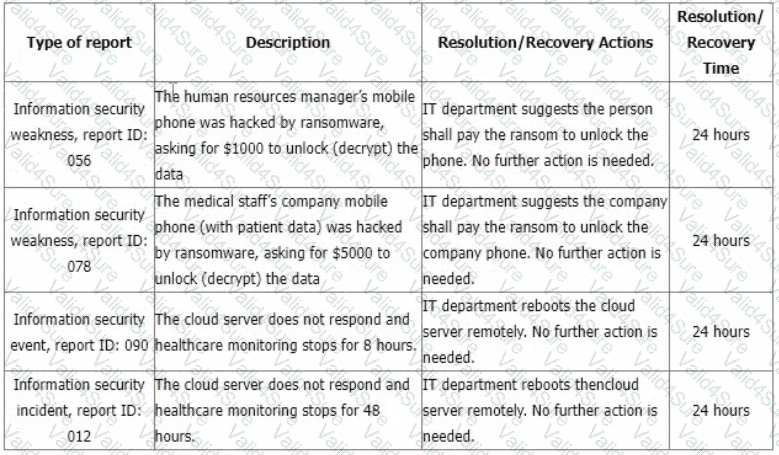
You would like to further investigate other areas to collect more audit evidence. Select two options that will not be in your audit trail.