ISO-IEC-27001-Lead-Auditor Exam Dumps - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Searching for workable clues to ace the PECB ISO-IEC-27001-Lead-Auditor Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s ISO-IEC-27001-Lead-Auditor PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You are performing an ISMS audit at a residential nursing home (ABC) that provides healthcare services. The next
step in your audit plan is to verify the information security of ABC's healthcare mobile app development, support,
and lifecycle process. During the audit, you learned the organization outsourced the mobile app development to a
professional software development company with CMMI Level 5, ITSM (ISO/IEC 20000-1), BCMS (ISO 22301) and
ISMS (ISO/IEC 27001) certified.
The IT Manager presented the software security management procedure and summarised the process as following:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a minimum.
The following security functions for personal data protection shall be available:
Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and
Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report, details as follows:
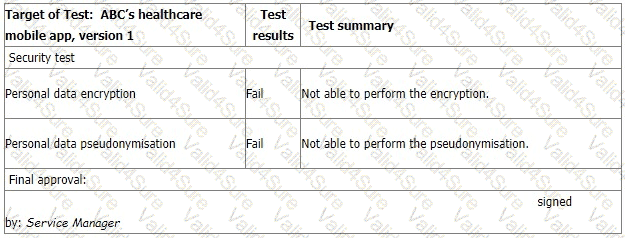
The IT Manager explains the test results should be approved by him according to the software security management procedure. The reason why the encryption and pseudonymisation functions failed is that these functions heavily slowed down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That's why the Service Manager signed the approval.
You are preparing the audit findings. Select the correct option.
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
According to Scenario 6, was it appropriate for the audit team to include in the audit report the observed deficiency in the marketing department's access rights control procedures?
Scenario 2
Knight is an electronics company based in Northern California, the US that develops video game consoles. With over 300 employees globally, Knight is celebrating its fifth anniversary by launching the G-Console, a next-generation gaming system aimed at international markets. G-Console is considered to be the ultimate media machine of 2021, and it will give players the best gaming experience. The console pack will include a pair of VR headsets, two games, and other gifts.
Over the years, the company has developed a strong reputation for integrity, honesty, and respect toward their customers. Besides being a very customer-oriented company, Knight also gained wide recognition within the gaming industry because of its quality.
As one of the leading video game console developers in the world, Knight often finds itself a target for malicious activities. Therefore, it has implemented an information security management system (ISMS) based on ISO/IEC 27001, and its scope was communicated to employees of the company over a weekly meeting.
Recently, however, Knight experienced a security breach when hackers leaked proprietary information. In response, the incident response team (IRT) immediately began a thorough investigation of the system and the specifics of the incident. Initially, the IRT suspected that employees may have used weak passwords, allowing hackers to easily access their accounts. Upon further investigation, it was revealed that the hackers captured traffic from the file transfer protocol (FTP), which transmits data using clear-text passwords for authentication.
In light of this security incident, and following the IRT’s recommendations, Knight decided to replace the FTP with Secure Shell (SSH) protocol. This change ensures that any captured traffic is encrypted, significantly improving security.
After implementing these changes, Knight conducted a risk assessment to verify that the implementation of controls had minimized the risk of similar incidents. Based on the results of the risk assessment, they chose a risk treatment option to treat the risk.
Question
Based on Scenario 2, the risk treatment option was based on the risk assessment results. Is this acceptable?
You are an experienced ISMS audit team leader conducting a third-party surveillance audit of an internet services provider. You are reviewing the organization's risk assessment processes for conformity with ISO/IEC 27001:2022.
Which three of the following audit findings would prompt you to raise a nonconformity report?
Scenario 4: SendPay is a financial company that provides its services through a network of agents and financial institutions. One of their main services is transferring money worldwide. SendPay, as a new company, seeks to offer top quality services to its clients. Since the company offers international transactions, it requires from their clients to provide personal information, such as their identity, the reason for the transactions, and other details that might be needed to complete the transaction. Therefore, SendPay has implemented security measures to protect their clients' information, including detecting, investigating, and responding to any information security threats that may emerge. Their commitment to offering secure services was also reflected during the ISMS implementation where the company invested a lot of time and resources.
Last year, SendPay unveiled their digital platform that allows money transactions through electronic devices, such as smartphones or laptops, without requiring an additional fee. Through this platform, SendPay's clients can send and receive money from anywhere and at any time. The digital platform helped SendPay to simplify the company's operations and further expand its business. At the time, SendPay was outsourcing its software operations, hence the project was completed by the software development team of the outsourced company. The same team was also responsible for maintaining the technology infrastructure of SendPay.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year. They contracted a certification body that fit their criteria. Soon after, the certification body appointed a team of four auditors to audit SendPay's ISMS.
During the audit, among others, the following situations were observed:
1.The outsourced software company had terminated the contract with SendPay without prior notice. As a result, SendPay was unable to immediately bring the services back in-house and its operations were disrupted for five days. The auditors requested from SendPay's representatives to provide evidence that they have a plan to follow in cases of contract terminations. The representatives did not provide any documentary evidence but during an interview, they told the auditors that the top management of SendPay had identified two other software development companies that could provide services immediately if similar situations happen again.
2.There was no evidence available regarding the monitoring of the activities that were outsourced to the software development company. Once again, the representatives of SendPay told the auditors that they regularly communicate with the software development company and that they are appropriately informed for any possible change that might occur.
3.There was no nonconformity found during the firewall testing. The auditors tested the firewall configuration in order to determine the level of security provided by
these services. They used a packet analyzer to test the firewall policies which enabled them to check the packets sent or received in real-time.
Based on this scenario, answer the following question:
Why could SendPay not restore their services back in-house after the contract termination? Refer to scenario 4.
You see a blue color sticker on certain physical assets. What does this signify?
According to ISO/IEC 27001, an Information Security Management System seeks to protect which two of the following?