400-007 Exam Dumps - Cisco Certified Design Expert (CCDE v3.1)
Searching for workable clues to ace the Cisco 400-007 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 400-007 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
What is a web-based model in which a third-party provider hosts applications that are available to customers over the Internet?
Refer to the exhibit.
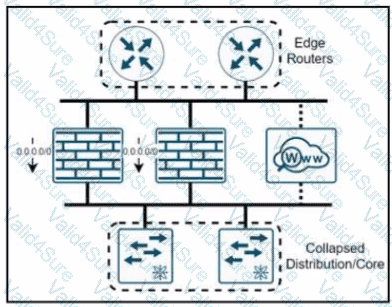
A company named XYZ needs to apply security policies for end-user browsing by installing a secure web proxy appliance. All the web traffic must be inspected by the appliance, and the remaining traffic must be inspected by an NGFW that has been upgraded with intrusion prevention system functionality. In which two ways must the routing be performed? (Choose two)
SD-WAN can be used to provide secure connectivity to remote offices, branch offices, campus networks, data centers, and the cloud over any type of IP-based underlay transport network. Which two statements describe SD-WAN solutions? (Choose two.)
Refer to the exhibit.
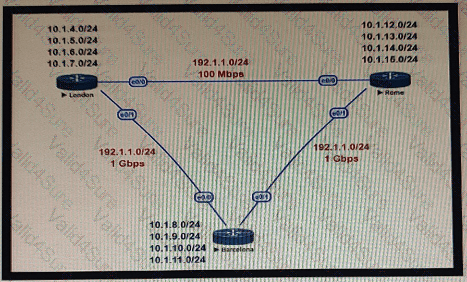
This network is running OSPF as the routing protocol. The internal networks are being advertised in OSPF. London and Rome are using the direct link to reach each other although the transfer rates are better via Barcelona. Which OSPF design change allows OSPF to calculate the proper costs?
An architect prepares a network design for a startup company. The design must meet business requirements while the business grows and divests due to rapidly changing markets. What is the highest priority in this design?
An enterprise wants to provide low-cost delivery of network systems that can be scaled on business demand, followed by an initiative to reduce capital expenses for new IT equipment. Which technology meets these goals?
What are two examples of business goals to be considered when a network design is built? (Choose two.)