200-301 Exam Dumps - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
Searching for workable clues to ace the Cisco 200-301 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 200-301 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which two tasks must be performed to configure NTP to a trusted server in client mode on a single network device? (Choose two)
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
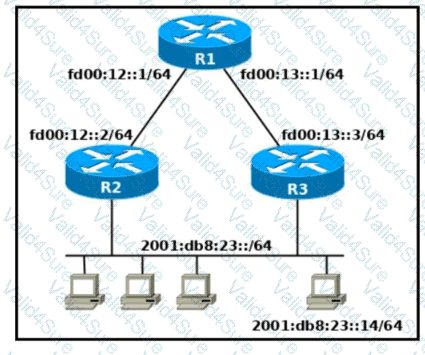
Refer to the exhibit. Which two commands, when configured on router R1. fulfill these requirements? (Choose two.) ' Packets toward the entire network 2001:db8:23: :/64 must be forwarded through router R2. ' Packets toward host 2001: db8:23::14 preferably must be forwarded through R3.
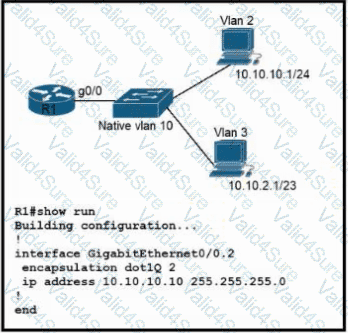
Refer to the exhibit. Configurations for the switch and PCs are complete.
Which configuration must be applied so that VLANs 2 and 3 communicate back and forth?

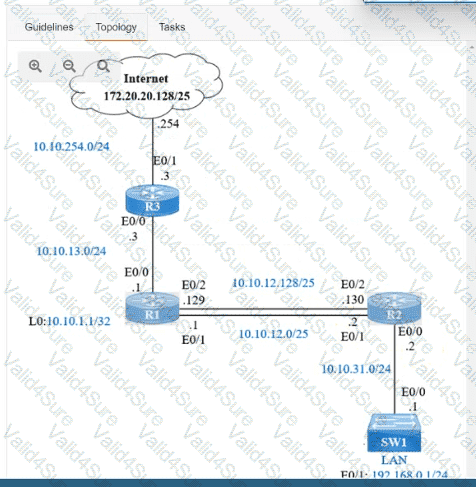
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.