200-301 Exam Dumps - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
Searching for workable clues to ace the Cisco 200-301 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 200-301 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
What uses HTTP messages to transfer data to applications residing on different hosts?
What are two roles of the Dynamic Host Configuration Protocol (DHCP)? (Choose two)
Which command prevents passwords from being stored in the configuration as plain text on a router or switch?
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
What is a network appliance that checks the state of a packet to determine whether the packet is legitimate?
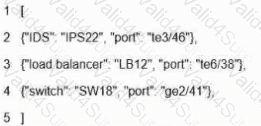
Refer to the exhibit.
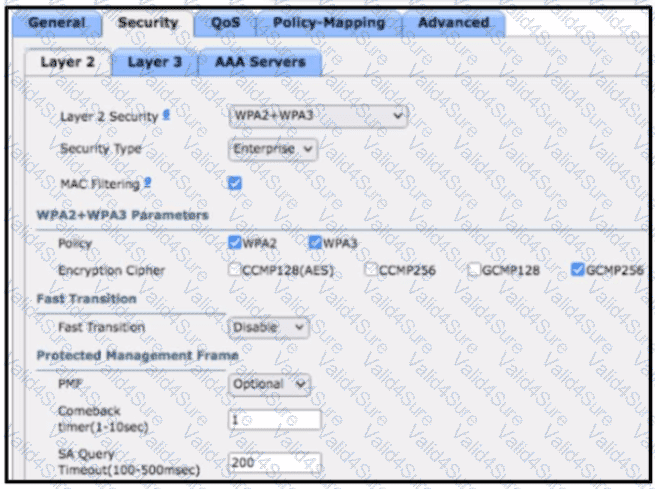
An engineer must document all Wi-Fi services on a new wireless LAN controller. The Wi-Fi SSID "Office_WLan" has Layer 2 Security. What is determined by this configuration?