H12-821_V1.0 Exam Dumps - HCIP-Datacom-Core Technology V1.0
Searching for workable clues to ace the Huawei H12-821_V1.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s H12-821_V1.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A session is an entry used to record the connection status of a protocol and is fundamental for the firewall to forward packets. Which of the following protocol packets will the firewall create sessions for?
When an SSH client accesses an SSH server for the first time and the SSH server's public key is not configured on the SSH client, you can enable first-time authentication on the SSH client. This allows the SSH client to access the SSH server and saves the SSH server's public key on the SSH client. In this way, the next time the SSH client accesses the SSH server, the SSH client can use the saved public key to authenticate the SSH server.
In addition to a route reflector, the confederation is another method that reduces the number of IBGP connections in an AS.
Which of the following statements are true about the confederation technology? (Choose all that apply)
On the OSPF network shown in the figure, an adjacency has been established between R1 and R2. An engineer configures the commands in the figure on R2. In this case, which of the following routing entries may exist in the routing table of R2?
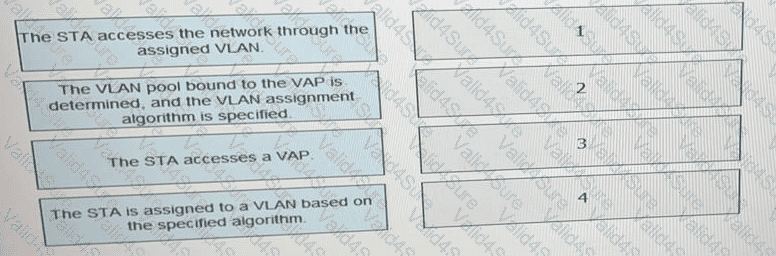
What is the correct procedure for a VLAN pool to assign terminals to VLANs.
BGP is a distance-vector protocol that implements route reachability between ASs and selects optimal routes. Which of the following statements are true about this protocol?
Which of the following methods is usually used by a network administrator to configure a newly purchased device for the first time?
In an IPv4 address space, Class D addresses are used for multicast. Among Class D addresses, which of the following is the permanent group address range reserved for routing protocols?