350-701 Exam Dumps - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Searching for workable clues to ace the Cisco 350-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which firewall mode does a Cisco Adaptive Security Appliance use to inspect Layer 2 traffic?
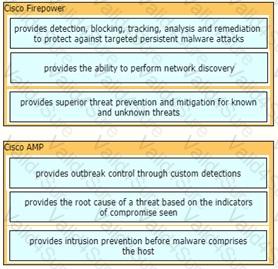
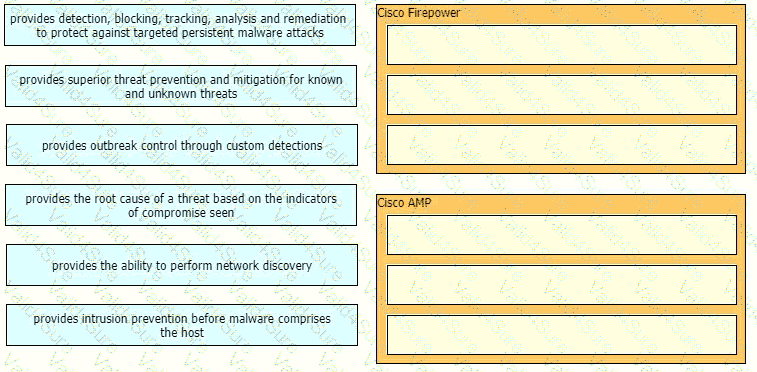
Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right.
What is the primary difference between an Endpoint Protection Platform and an Endpoint Detection and
Response?
What is a functional difference between a Cisco ASA and a Cisco IOS router with Zone-based policy firewall?
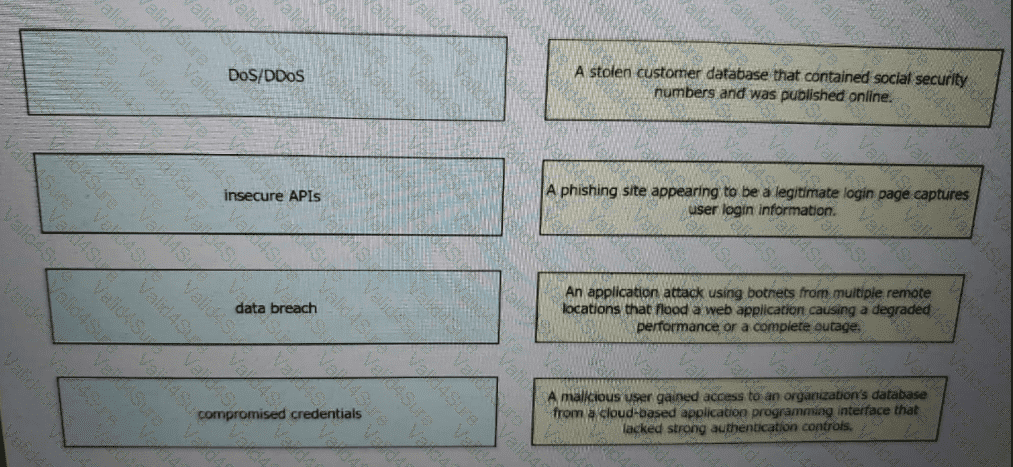
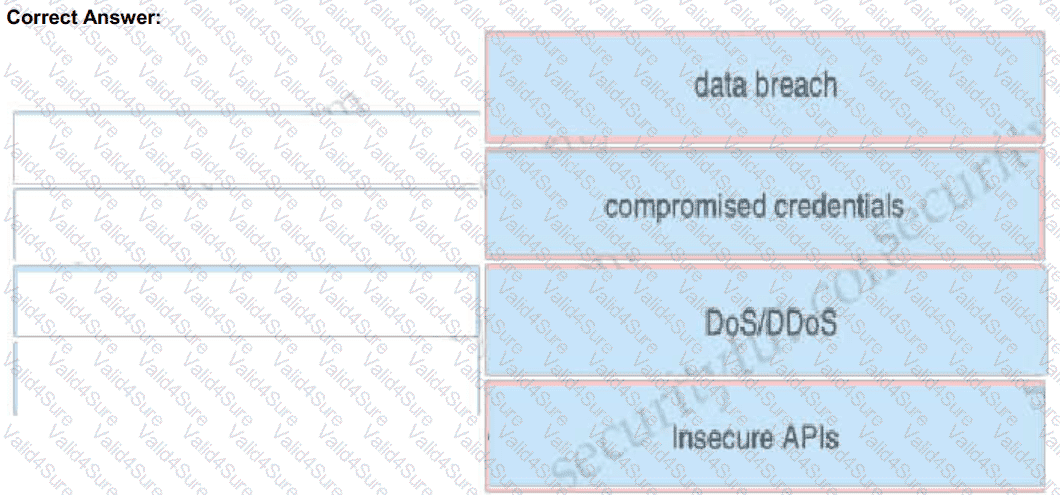
Drag and drop the threats from the left onto examples of that threat on the right