200-301 Exam Dumps - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
Searching for workable clues to ace the Cisco 200-301 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 200-301 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.
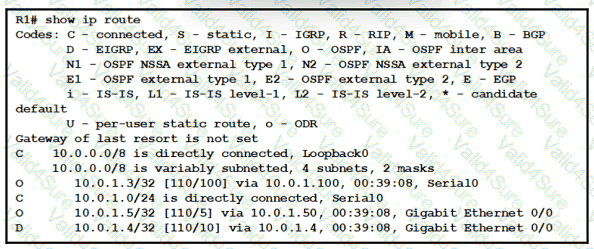
What does route 10.0.1.3/32 represent in the routing table?
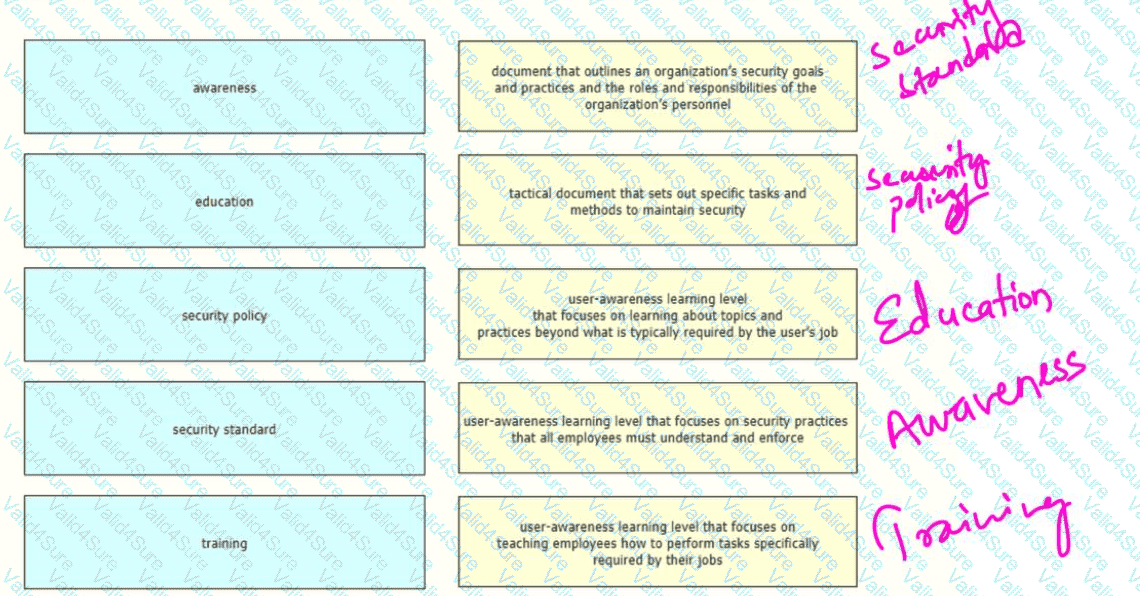
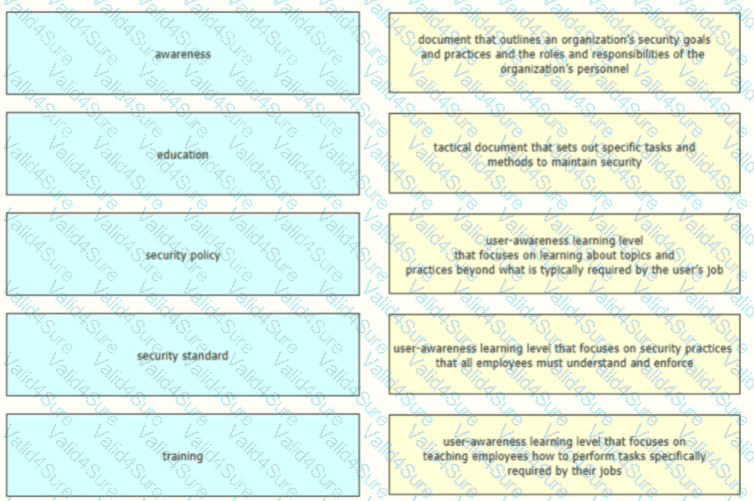
Drag and drop the elements of a security program from the left onto the corresponding descriptions on the right.
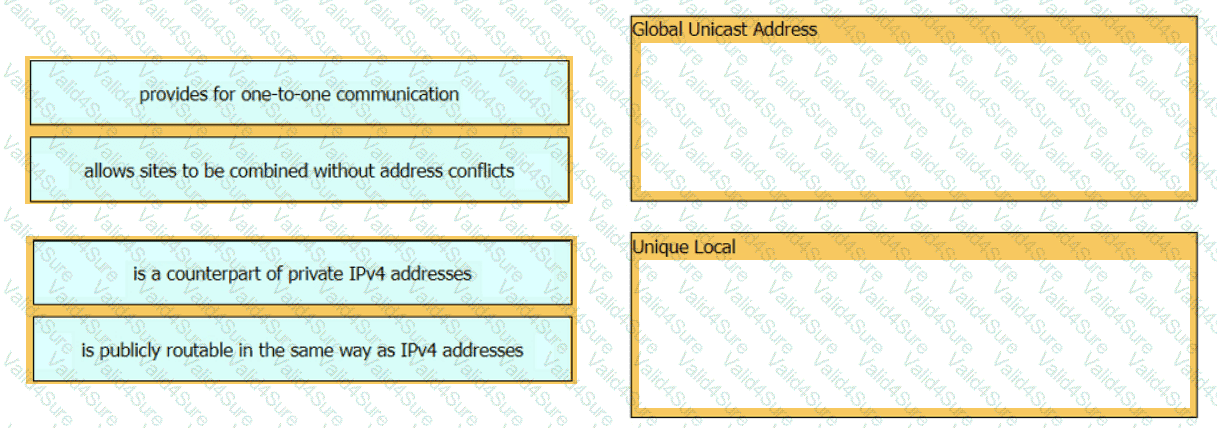
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Refer to the exhibit.
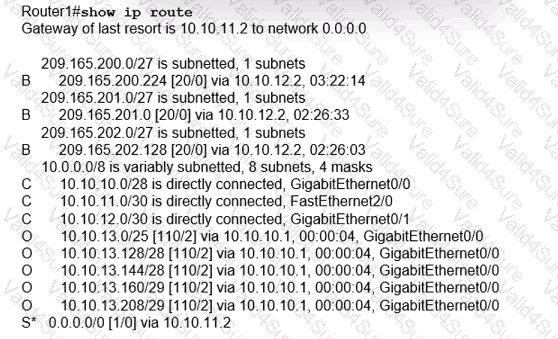
What is the subnet mask of the route to the 10.10.13.160 prefix?

Refer to the exhibit. Users at a branch office are experiencing application performance issues, poor VoIP audio quality, and slow downloads. What is the cause of the issues?