XK0-005 Exam Dumps - CompTIA Linux+ Exam
Searching for workable clues to ace the CompTIA XK0-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s XK0-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A Linux systems administrator is configuring a new filesystem that needs the capability to be mounted persistently across reboots. Which of the following commands will accomplish this task? (Choose two.)
Junior system administrator had trouble installing and running an Apache web server on a Linux server. You have been tasked with installing the Apache web server on the Linux server and resolving the issue that prevented the junior administrator from running Apache.
INSTRUCTIONS
Install Apache and start the service. Verify that the Apache service is running with the defaults.
Typing “help†in the terminal will show a list of relevant event commands.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An administrator attempts to rename a file on a server but receives the following error.
The administrator then runs a few commands and obtains the following output:
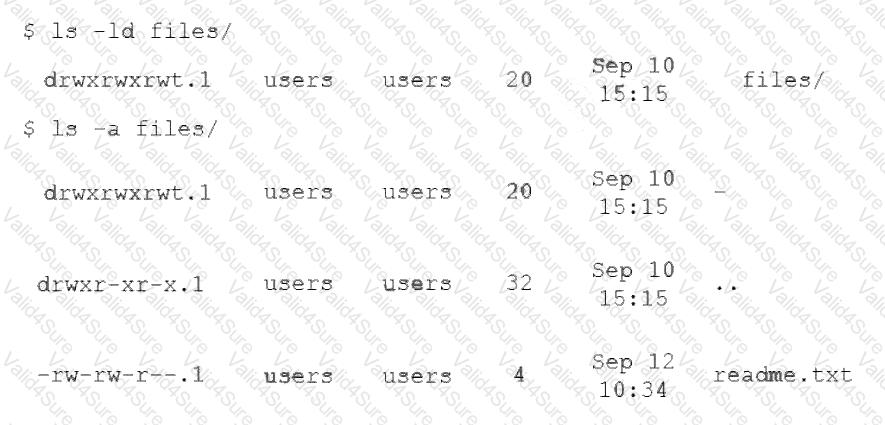
Which of the following commands should the administrator run NEXT to allow the file to be renamed by any user?
To harden one of the servers, an administrator needs to remove the possibility of remote administrative login via the SSH service. Which of the following should the administrator do?
A Linux administrator wants to find out whether files from the wget package have been altered since they were installed. Which of the following commands will provide the correct information?
A Linux administrator is troubleshooting SSH connection issues from one of the workstations.
When users attempt to log in from the workstation to a server with the IP address 104.21.75.76, they receive the following message:
The administrator reviews the information below:
Which of the following is causing the connectivity issue?
NO: 41:
A systems administrator needs to install the file installer_0.17-41.2_amd64.deb. Which of the following commands should the administrator use?
A systems administrator receives the following message after running an ip link command to verify the status of a network interface named enp0s3:
state DOWN
Which of the following commands should the administrator use to resolve this issue?