SY0-701 Exam Dumps - CompTIA Security+ Exam 2025
Searching for workable clues to ace the CompTIA SY0-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SY0-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A security administrator is implementing encryption on all hard drives in an organization. Which of the following security concepts is the administrator applying?
Which of the following data types best describes an AI tool developed by a company to automate the ticketing system under a specific contract?
Which of the following environments utilizes a subset of customer data and is most likely to be used to assess the impacts of major system upgrades and demonstrate system features?
Which of the following phases of the incident response process attempts to minimize disruption?
An organization is evaluating the cost of licensing a new solution to prevent ransomware. Which of the following is the most helpful in making this decision?
An administrator wants to automate an account permissions update for a large number of accounts. Which of the following would best accomplish this task?
A company is developing a critical system for the government and storing project information on a fileshare. Which of the following describes how this data will most likely be classified? (Select two).
You are security administrator investigating a potential infection on a network.
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.
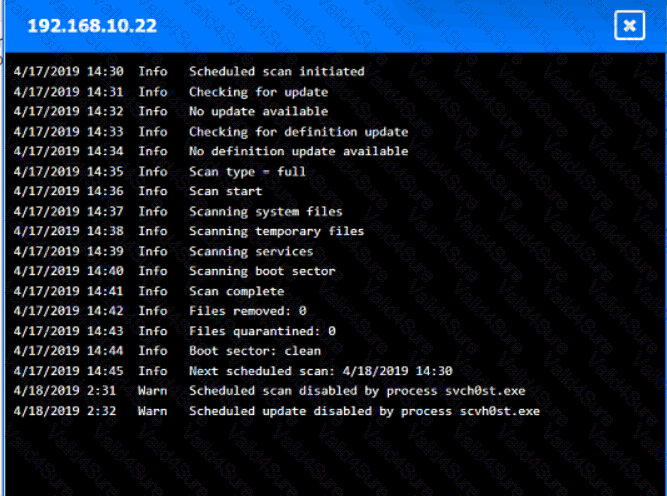
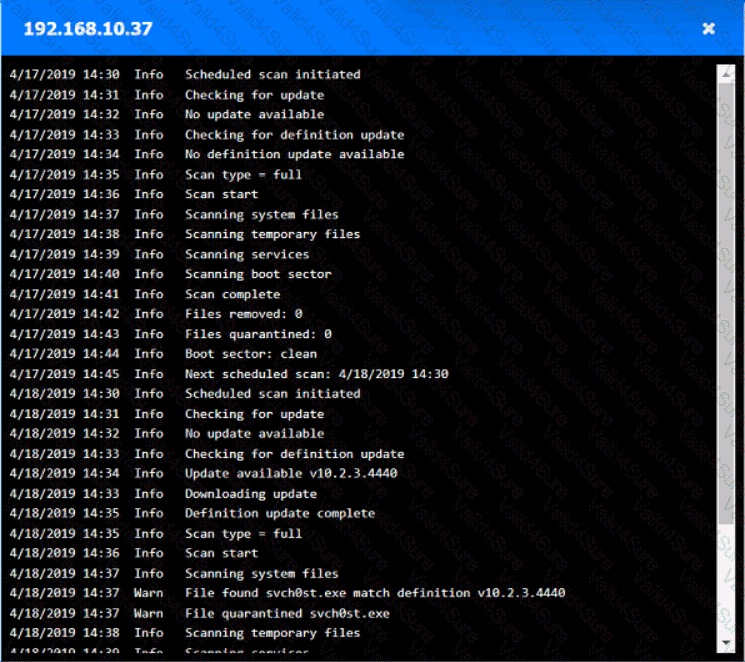
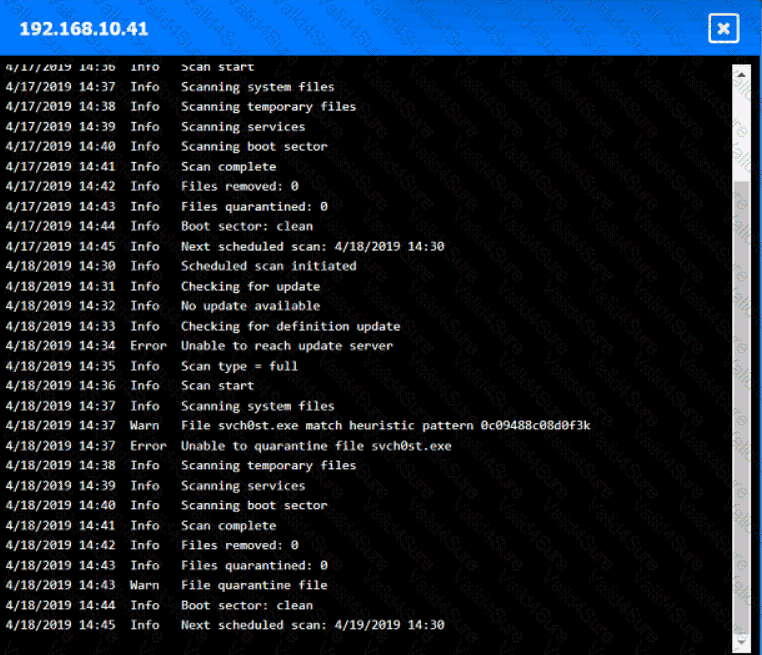
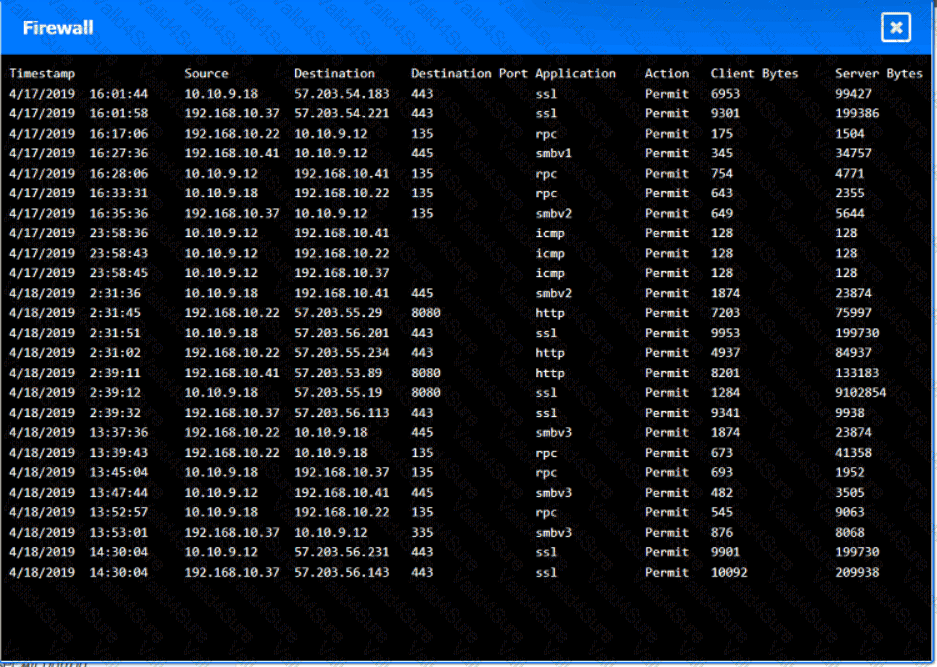
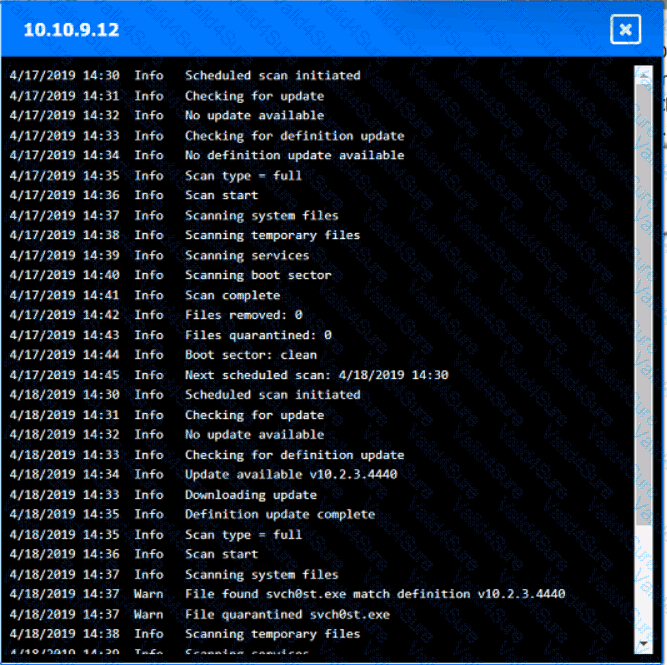
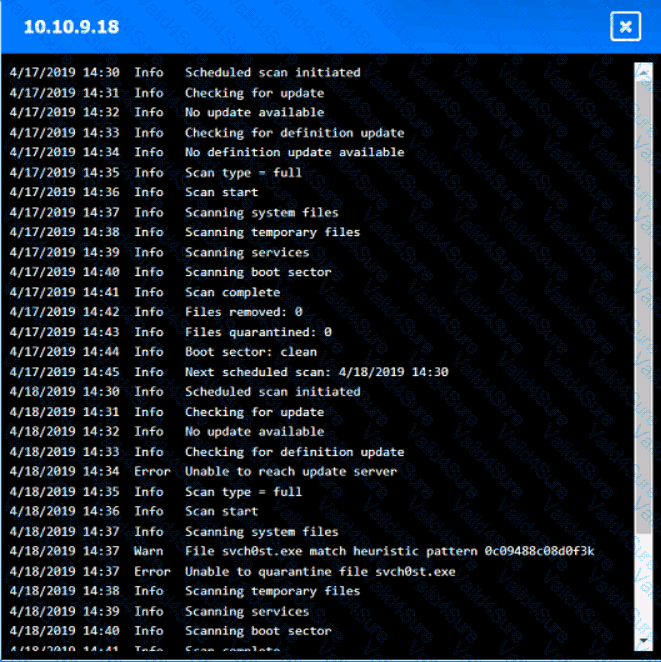
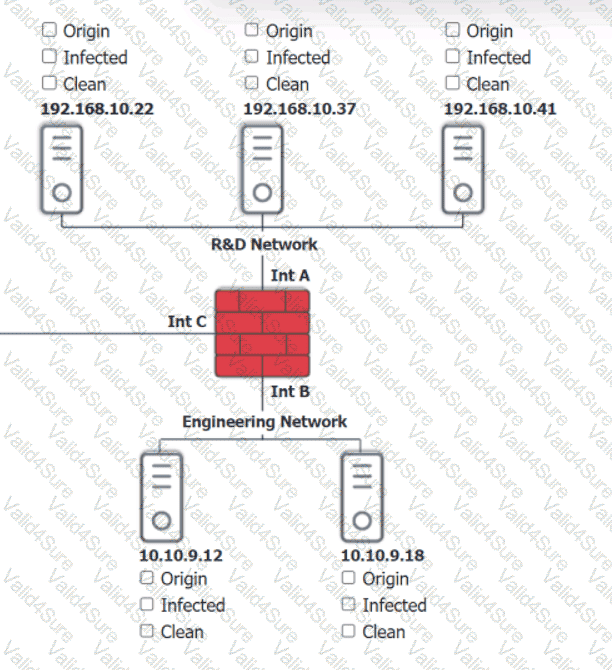
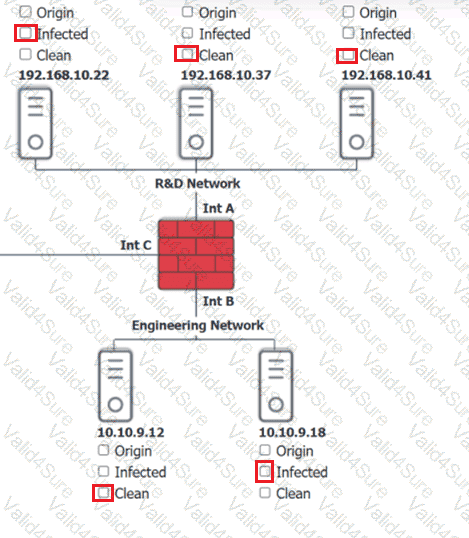 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.