SY0-701 Exam Dumps - CompTIA Security+ Exam 2025
Searching for workable clues to ace the CompTIA SY0-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SY0-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A network engineer is increasing the overall security of network devices and needs to harden the devices. Which of the following will best accomplish this task?
Which of the following is the greatest advantage that network segmentation provides?
A systems administrator works for a local hospital and needs to ensure patient data is protected and secure. Which of the following data classifications should be used to secure patient data?
Which of the following elements of digital forensics should a company use If It needs to ensure the integrity of evidence?
A bank set up a new server that contains customers' Pll. Which of the following should the bank use to make sure the sensitive data is not modified?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
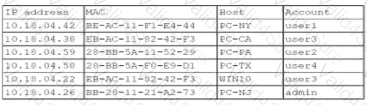
Which of the following is the most likely way a rogue device was allowed to connect?
A new employee logs in to the email system for the first time and notices a message from human resources about onboarding. The employee hovers over a few of the links within the email and discovers that the links do not correspond to links associated with the company. Which of the following attack vectors is most likely being used?