SY0-701 Exam Dumps - CompTIA Security+ Exam 2025
Searching for workable clues to ace the CompTIA SY0-701 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SY0-701 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
An administrator needs to perform server hardening before deployment. Which of the following steps should the administrator take? (Select two).
Which of the following activities is included in the post-incident review phase?
A security analyst needs to propose a remediation plan 'or each item in a risk register. The item with the highest priority requires employees to have separate logins for SaaS solutions and different password complexity requirements for each solution. Which of the following implementation plans will most likely resolve this security issue?
A security analyst locates a potentially malicious video file on a server and needs to identify both the creation date and the file's creator. Which of the following actions would most likely give the security analyst the information required?
A software developer would like to ensure. The source code cannot be reverse engineered or debugged. Which of the following should the developer consider?
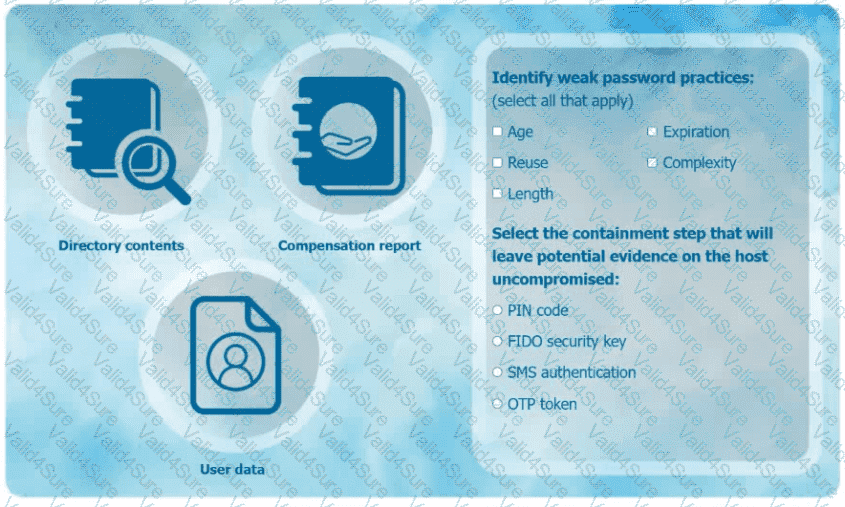
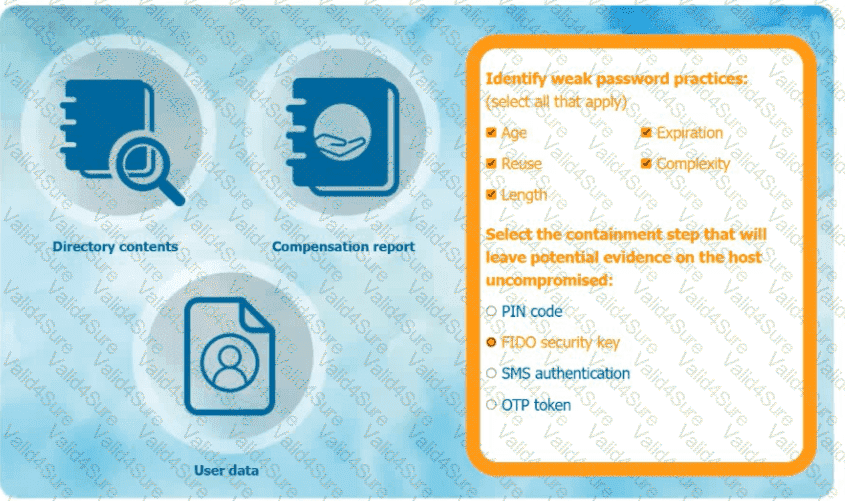
An organization has learned that its data is being exchanged on the dark web. The CIO
has requested that you investigate and implement the most secure solution to protect employee accounts.
INSTRUCTIONS
Review the data to identify weak security practices and provide the most appropriate
security solution to meet the CIO's requirements.
Which of the following must be considered when designing a high-availability network? (Choose two).
 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.