SC-401 Exam Dumps - Administering Information Security in Microsoft 365
Searching for workable clues to ace the Microsoft SC-401 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SC-401 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You have a Microsoft SharePoint Online site named Site! that contains the files shown in the following table.

You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
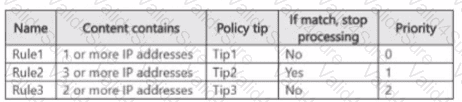
You apply DLP1 toSite1.
Which policy tips will appear for File2?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 11. The computers are onboarded to Microsoft Purview.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft Defender for Cloud Apps, you mark the application as Unsanctioned.
Does this meet the goal?
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You need to deploy a compliance solution that will detect the accidental oversharing of information outside of an organization.
The solution must minimize administrative effort.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
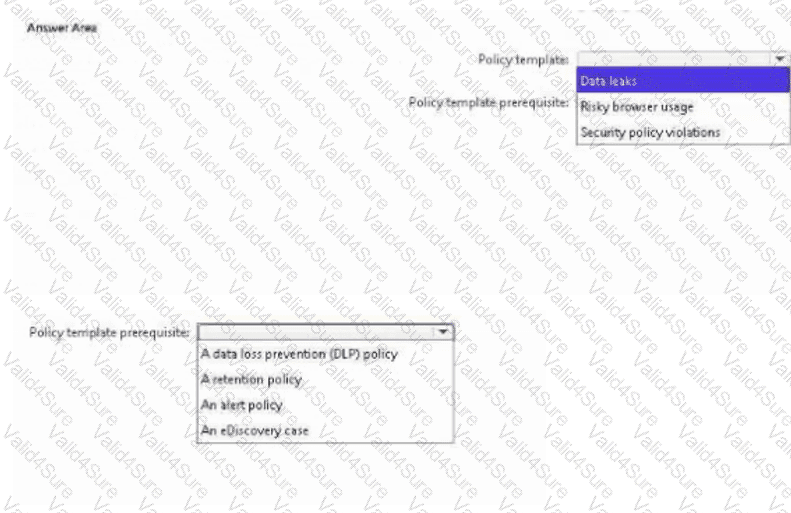
You have a Microsoft 365 subscription that contains two Microsoft SharePoint Online sites named Site1 and Site2. You plan to use policies to meet the following requirements:
• Add a watermark of Confidential to a document if the document contains the words Project1 or Project2.
• Retain a document for seven years if the document contains credit card information.
• Add a watermark of Internal Use Only to all the documents stored on Site2.
• Add a watermark of Confidential to all the documents stored on Site1.
You need to recommend the minimum number of sensitive info types required.
How many sensitive info types should you recommend?
You have a Microsoft 365 E5 subscription. The subscription contains 500 devices that are onboarded to Microsoft Purview.
You select Activate Microsoft Purview Audit.
You need to ensure that you can track interactions between users and generative AI websites.
What should you deploy to the devices?
You have a Microsoft 365 E5 subscription. The subscription contains a user named User1 and the sensitivity labels shown in the following table.

You publish the labels to User1.
The subscription contains the files shown in the following table.
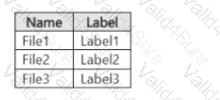
Which files can Microsoft 365 Copilot summarize for User1?
Nate: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique
solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might
not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the
review screen.
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 11 and have Microsoft 365 Apps installed. The computers are joined to a Microsoft Entra tenant.
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender for Endpoint.
Does this meet the goal?
You have a Microsoft 365 E5 subscription.
You create a sensitivity label named Label1 and publish Label1 to all users and groups.
You have the following files in a SharePoint site:
• File1.doc
• File2.docx
• File3.xlsx
• File4.txt
You need to identify which files can have Label1 applied.
Which files should you identify?