SC-401 Exam Dumps - Administering Information Security in Microsoft 365
Searching for workable clues to ace the Microsoft SC-401 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SC-401 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
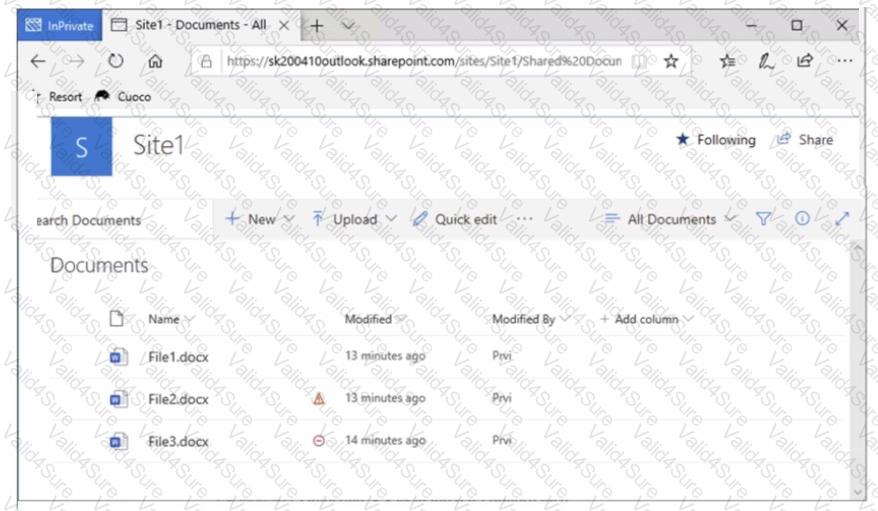
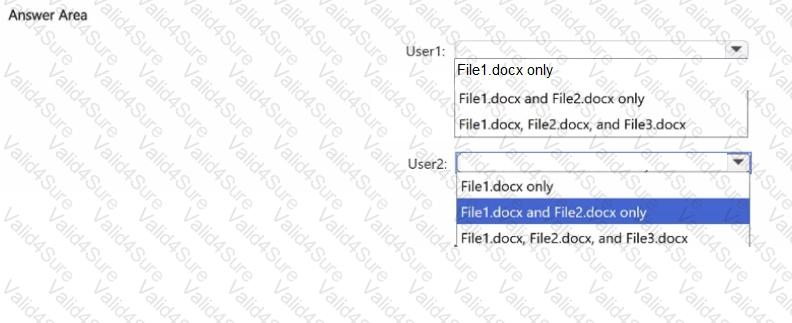
You have a Microsoft 365 E5 tenant that contains two users named User1, and User2 and a Microsoft SharePoint Online site named Site! as shown in the following exhibit.
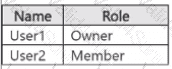
For Site1, the users are assigned the roles shown in the following table.
You publish a retention label named Retention1 to Site1.
To which files can the users apply Retention!? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the sensitive information types (SITs) shown in the following table.
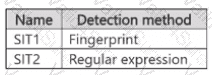
You plan to create the policies shown in the following table and assign them to a Microsoft SharePoint Online site.

Which policies can use SIT1. and which policies can use SIT2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 tenant.
You need to add a new keyword dictionary.
What should you create?
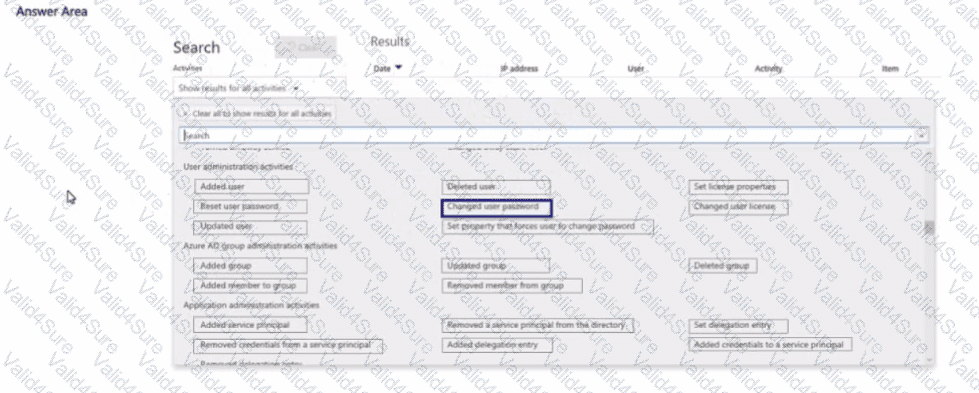
You have a Microsoft 365 subscription. Auditing is enabled.
A user named User1 is a member of a dynamic security group named Group1.
You discover that User1 is no longer a member of Group1.
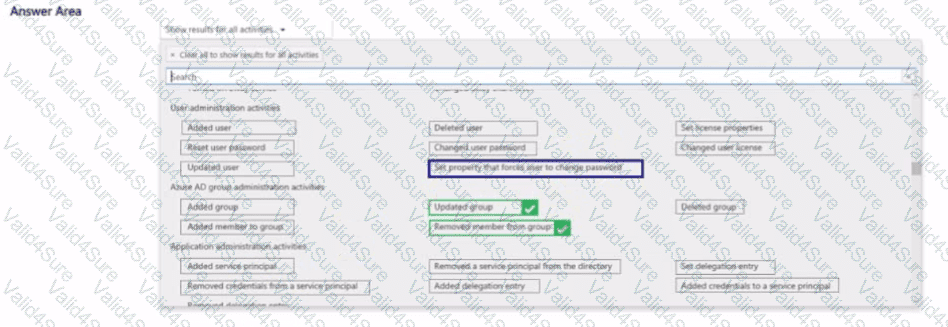
You need to search the audit log to identify why User1 was removed from Group1.
Which two activities should you use in the search? To answer, select the appropriate activities in the answer area.
NOTE: Each correct selection is worth one point.
You have Microsoft 365 E5 subscription that uses data loss prevention (DLP) to protect sensitive information.
You have a document named Form.docx.
You plan to use PowerShell to create a document fingerprint based on Form.docx.
You need to first connect to the subscription.
Which cmdlet should you run?
You have Microsoft 365 E5 subscription.
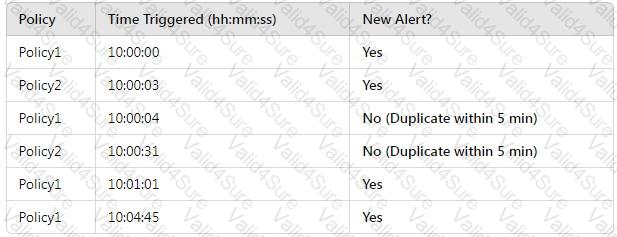
You create two alert policies named Policy1 and Policy2 that will be triggered at the times shown in the following table.
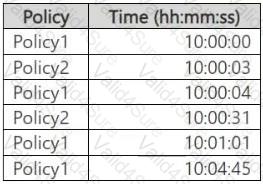
How many alerts will be added to the Microsoft Purview portal?
You are creating a custom trainable classifier to Identify organizational product codes referenced in Microsoft 36S content. You identify 300 files to use as seed content When? should you store the seed content?
You have a Microsoft 365 E5 subscription.
You need to ensure that encrypted email messages sent to an external recipient can be revoked or will expire within seven days.
What should you configure first?