Practitioner Exam Dumps - Palo Alto Networks Cybersecurity Practitioner (PCCP)
Searching for workable clues to ace the Paloalto Networks Practitioner Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s Practitioner PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
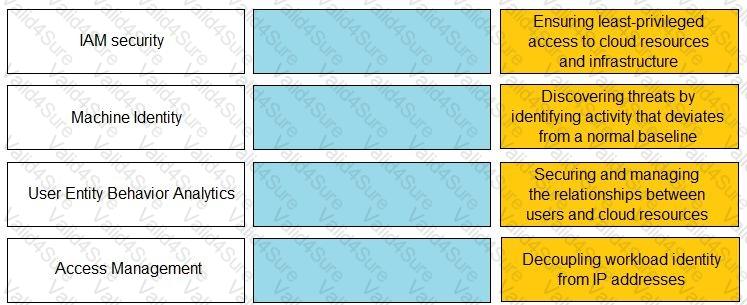
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Which characteristic of serverless computing enables developers to quickly deploy application code?
Which scenario highlights how a malicious Portable Executable (PE) file is leveraged as an attack?
An administrator finds multiple gambling websites in the network traffic log.
What can be created to dynamically block these websites?
What does Palo Alto Networks Cortex XDR do first when an endpoint is asked to run an executable?
Which internet of things (loT) connectivity technology operates on the 2.4GHz and 5GHz bands, as well as all bands between 1 and 6GHz when they become available for 802.11 use. at ranges up to 11 Gbit/s?