NSE7_OTS-7.2 Exam Dumps - Fortinet NSE 7 - OT Security 7.2
Searching for workable clues to ace the Fortinet NSE7_OTS-7.2 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE7_OTS-7.2 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit, which shows a non-protected OT environment.
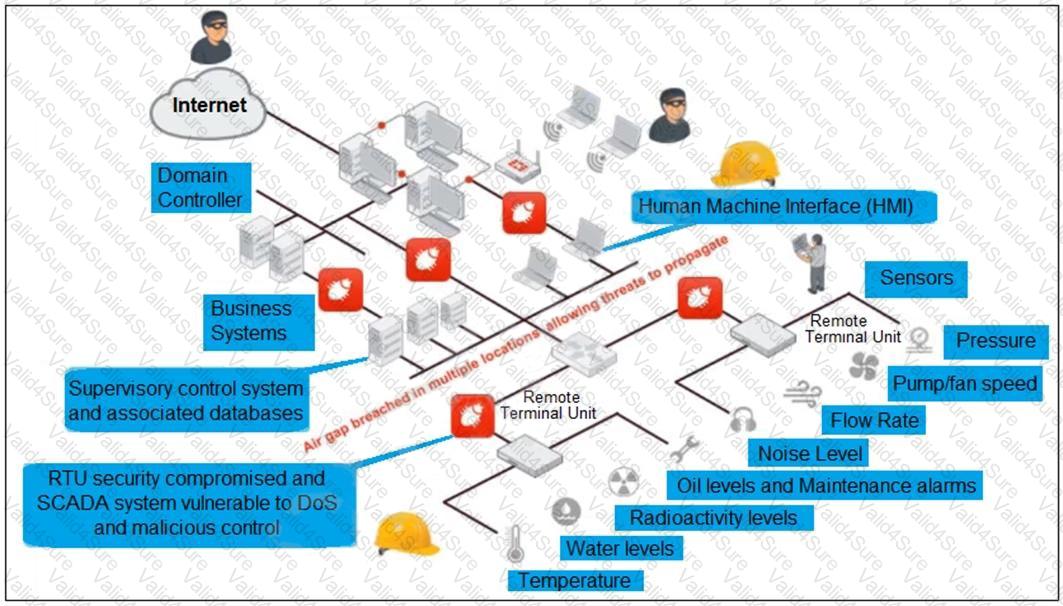
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
What triggers Layer 2 polling of infrastructure devices connected in the network?
Refer to the exhibit.
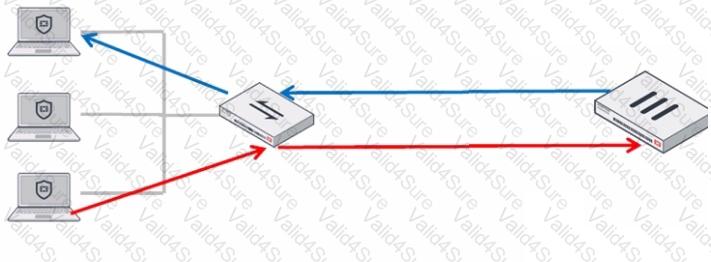
In order for a FortiGate device to act as router on a stick, what configuration must an OT network architect implement on FortiGate to achieve inter-VLAN routing?
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)