NSE7_OTS-7.2 Exam Dumps - Fortinet NSE 7 - OT Security 7.2
Searching for workable clues to ace the Fortinet NSE7_OTS-7.2 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE7_OTS-7.2 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
Which type of attack posed by skilled and malicious users of security level 4 (SL 4) of IEC 62443 is designed to defend against intentional attacks?
Refer to the exhibit.
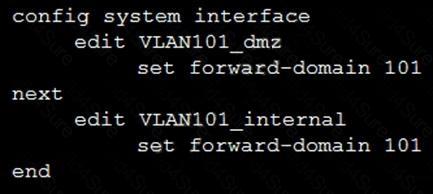
Given the configurations on the FortiGate, which statement is true?
Which statement is correct about processing matched rogue devices by FortiNAC?
Which three common breach points can you find in a typical OT environment? (Choose three.)
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
Refer to the exhibit and analyze the output.
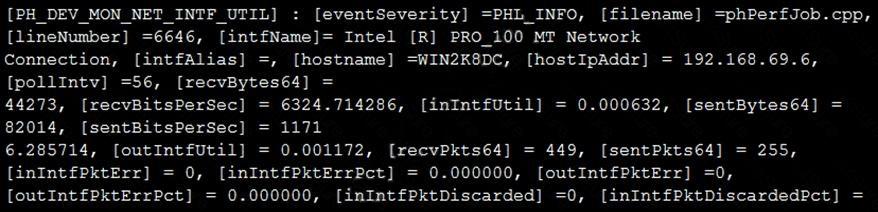
Which statement about the output is true?