NSE7_EFW-7.0 Exam Dumps - Fortinet NSE 7 - Enterprise Firewall 7.0
Searching for workable clues to ace the Fortinet NSE7_EFW-7.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE7_EFW-7.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A FortiGate has two default routes:
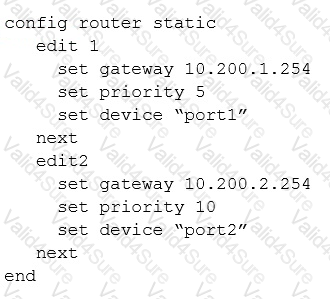
All Internet traffic is currently using port1. The exhibit shows partial information for one sample session of Internet traffic from an internal user:
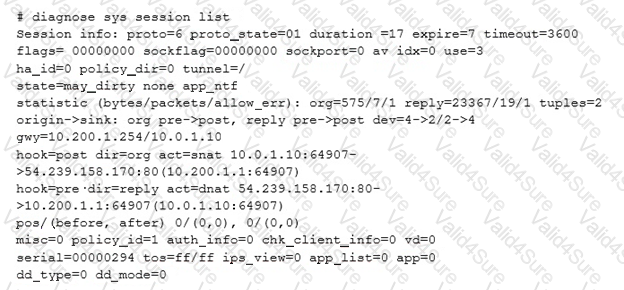
What would happen with the traffic matching the above session if the priority on the first default route (IDd1) were changed from 5 to 20?
View the IPS exit log, and then answer the question below.
# diagnose test application ipsmonitor 3
ipsengine exit logâ€
pid = 93 (cfg), duration = 5605322 (s) at Wed Apr 19 09:57:26 2017
code = 11, reason: manual
What is the status of IPS on this FortiGate?
Examine the output from the BGP real time debug shown in the exhibit, then the answer the question below:
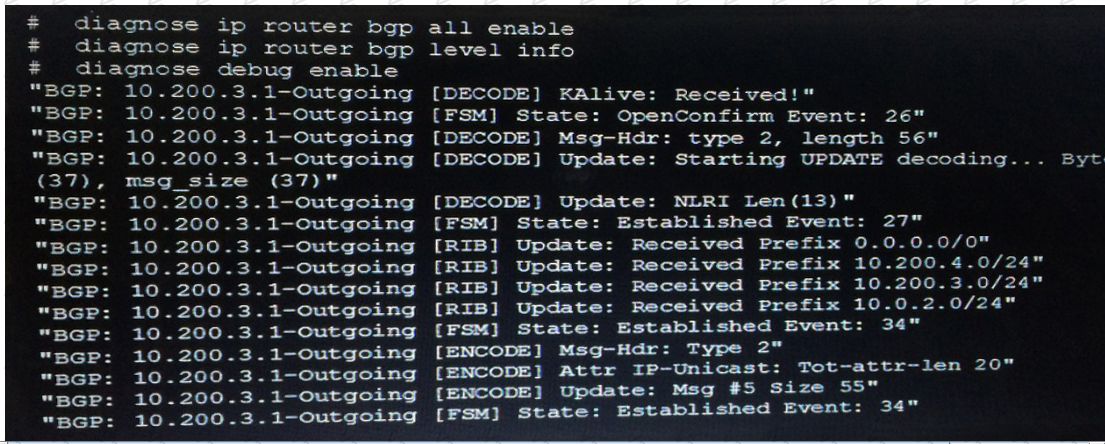
Which statements are true regarding the output in the exhibit? (Choose two.)