HPE6-A78 Exam Dumps - Aruba Certified Network Security Associate Exam
Searching for workable clues to ace the HP HPE6-A78 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s HPE6-A78 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit, which shows the current network topology.
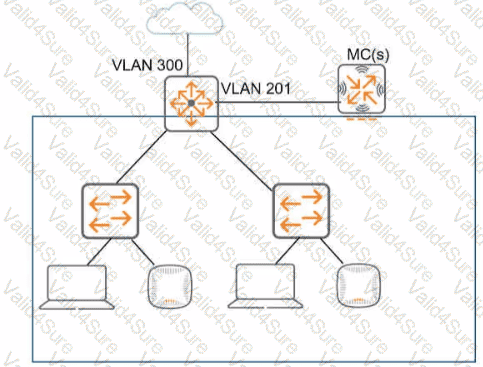
You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility Controllers (MCs). and campus APs (CAPs). The solution will Include a WLAN that uses Tunnel for the forwarding mode and Implements WPA3-Enterprise security
What is a guideline for setting up the vlan for wireless devices connected to the WLAN?
You have detected a Rogue AP using the Security Dashboard Which two actions should you take in responding to this event? (Select two)
You have been asked to send RADIUS debug messages from an AOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command:
logging 10.5.15.6
You enter this command:
debug radius all
What is the correct debug destination?
You have been authorized to use containment to respond to rogue APs detected by ArubaOS Wireless Intrusion Prevention (WIP). What is a consideration for using tarpit containment versus traditional wireless containment?
Device A is contacting https://arubapedia.arubanetworks.com. The web server sends a certificate chain. What does the browser do as part of validating the web server certificate?