HPE6-A78 Exam Dumps - Aruba Certified Network Security Associate Exam
Searching for workable clues to ace the HP HPE6-A78 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s HPE6-A78 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You are deploying an Aruba Mobility Controller (MC). What is a best practice for setting up secure management access to the ArubaOS Web UP
What is a guideline for creating certificate signing requests (CSRs) and deploying server Certificates on ArubaOS Mobility Controllers (MCs)?
Refer to the exhibit.
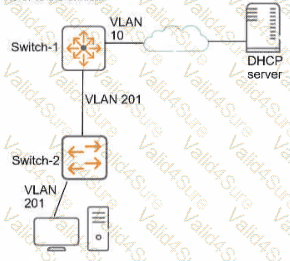
This company has ArubaOS-Switches. The exhibit shows one access layer switch, Swllcn-2. as an example, but the campus actually has more switches. The company wants to slop any internal users from exploiting ARP
What Is the proper way to configure the switches to meet these requirements?
Refer to the exhibit.
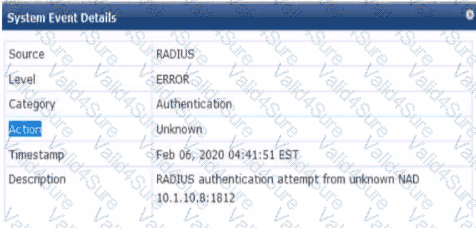
You are deploying a new ArubaOS Mobility Controller (MC), which is enforcing authentication to Aruba ClearPass Policy Manager (CPPM). The authentication is not working correctly, and you find the error shown In the exhibit in the CPPM Event Viewer.
What should you check?
What is one of the policies that a company should define for digital forensics?
You need to set up Aruba network infrastructure devices for management with SNMP. The SNMP server has this SNMPv3 user configured on it: username: airwave auth algorithm: sha auth key: fyluqp18@S!9a priv algorithm: aes priv key: 761oxaiaoeu19&
What correctly describes the setup on the infrastructure device?