CV0-004 Exam Dumps - CompTIA Cloud+ (2025)
Searching for workable clues to ace the CompTIA CV0-004 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CV0-004 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following cloud deployment strategies is best for an organization that wants to run open-source workloads with other organizations that are sharing the cost?
A cloud engineer needs to migrate an application from on premises to a public cloud. Due to timing constraints, the application cannot be changed prior to migration. Which of the
following migration strategies is best approach for this use case?
A company's website suddenly crashed. A cloud engineer investigates the following logs:
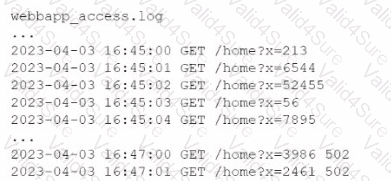
Which of the following is the most likely cause of the issue?
A cloud engineer is designing a high-performance computing cluster for proprietary software. The software requires low network latency and high throughput between cluster nodes.
Which of the following would have the greatest impact on latency and throughput when designing the HPC infrastructure?
The change control board received a request to approve a configuration change 10 deploy in the cloud production environment. Which of the following should have already been competed?