CV0-004 Exam Dumps - CompTIA Cloud+ (2025)
Searching for workable clues to ace the CompTIA CV0-004 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CV0-004 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A cloud engineer is developing an operating expense report that will be used to purchase various cloud billing models for virtual machine instances. The cloud billing model must meet the following requirements:
• The instance cannot be ephemeral.
• The minimum life cycle of the instance is expected to be five years.
• The software license is charged per physical CPU count.
Which of the following models would best meet these requirements?
A newly configured VM fails to run application updates despite having internet access. The updates download automatically from a third-party network. Given the following output:
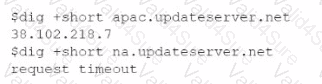
Which of the following troubleshooting steps would be best to take?
A customer is migrating applications to the cloud and wants to grant authorization based on the classification levels of each system. Which of the following should the customer implement to ensure authorisation to systems is granted when the user and system classification properties match? (Select two).
A cloud solutions architect needs to design a solution that will collect a report and upload it to an object storage service every time a virtual machine is gracefully or non-gracefully
stopped. Which of the following will best satisfy this requirement?
A project team is reviewing the project plan and related documents and identifies tasks that could be spread into smaller deliverables. Which of the following documents should the team edit first?
Users report being unable to access an application that uses TLS 1.1. The users are able to access other applications on the internet. Which of the following is the most likely
reason for this issue?
An IT security team wants to ensure that the correct parties are informed when a specific user account is signed in. Which of the following would most likely allow an administrator to address this concern?
An administrator received a report that company data has been compromised. The compromise occurred on a holiday, and no one in the organization was working. While reviewing
the logs from the holiday, the administrator noted the following details:
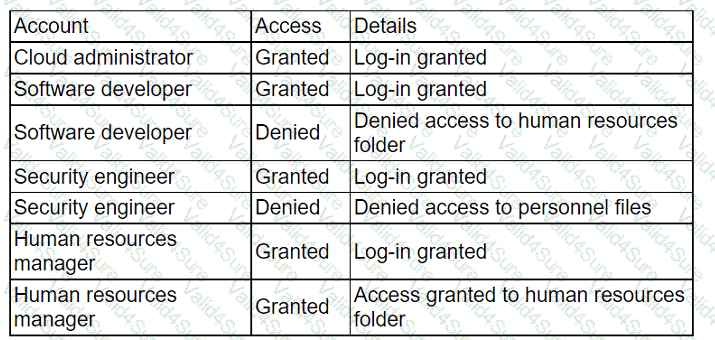
The most appropriate action for the cloud security analyst to recommend is using CIS-hardened images. These images are pre-configured by the Center for Internet Security to provide security benchmark standards that help in mitigating vulnerabilities in publicly available container images. References: CompTIA Cloud+ Study Guide (Exam CV0-004) - Chapter on Cloud Security Posture
Which of the following accounts should the administrator disable to prevent a further breach?