CPIM-8.0 Exam Dumps - Certified in Planning and Inventory Management (CPIM 8.0)
Searching for workable clues to ace the APICS CPIM-8.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CPIM-8.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following MUST exist for an activity to be considered an audit?
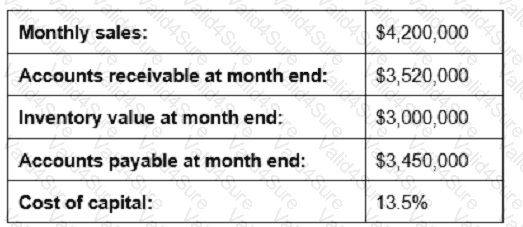
Given the information below, reducing which measure by 10% would contribute most to shortening the cash-to-cash cycle time?
The demand for an item has increasing forecast error, whereas all other factors remain constant. Which of the following remains constant while maintaining the same customer service level?
An organization is considering options to outsource their Information Technology (IT) operations. Although they do not sell anything on the Internet, they have a strong requirement in uptime of their application. After evaluating the offerings received by the Cloud Service Provider (CSP), the IT manager decided it was mandatory to develop processes to continue operations without access to community or public cloud-based applications. Which of the following arguments MOST likely led the IT manager to make this decision?
Zombieload, Meltdown, Spectre, and Fallout are all names of bugs that utilized which of the following types of attack?
A traffic analysis on an organization's network identifies a significant degree of inefficient resource use as a result of broadcast traffic. The organization wants to reduce the scope of the broadcasts without impeding the flow of traffic. Which of the following devices is the BEST choice to implement to achieve this goal?
Which of the below represent the GREATEST cloud-specific policy and organizational risk?