CPIM-8.0 Exam Dumps - Certified in Planning and Inventory Management (CPIM 8.0)
Searching for workable clues to ace the APICS CPIM-8.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CPIM-8.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following tools is used to evaluate the impact that a production plan has on capacity?
When designing a production cell, which of the following items would be the most important consideration?
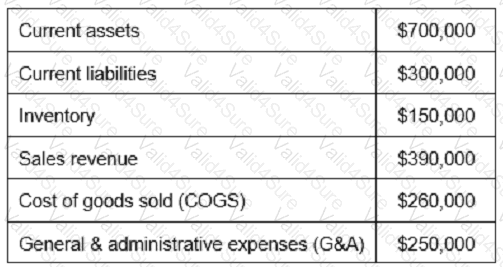
Based on the values reported in the table below, what is the inventory turnover?
What is the MOST likely cause for a penetration tester having difficulties finding the stack to inject code?
If fixed costs are §200,000 and 20,000 units are produced, a unit's fixed cost is §10. This is an example of:
Which of the following BEST describes the responsibility of an information System Security Officer?
Who is ultimately responsible for ensuring that specific data is protected?
Privacy requirements across national boundaries MOST often require protection of which data types?