350-901 Exam Dumps - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
Searching for workable clues to ace the Cisco 350-901 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-901 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Users report that they are no longer able to process transactions with the online ordering application, and the logging dashboard is
displaying these messages:
Fri Jan 10 19:37:31.123 ESI 2020 [FRONTEND] [NFO: Incoming request to add item to cart from user 45834534858
Fri Jan 10 19:37:31.247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31.250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused
What is causing the problem seen in these log messages?
Click on the GET Resource button above to view resources that will help with this question.
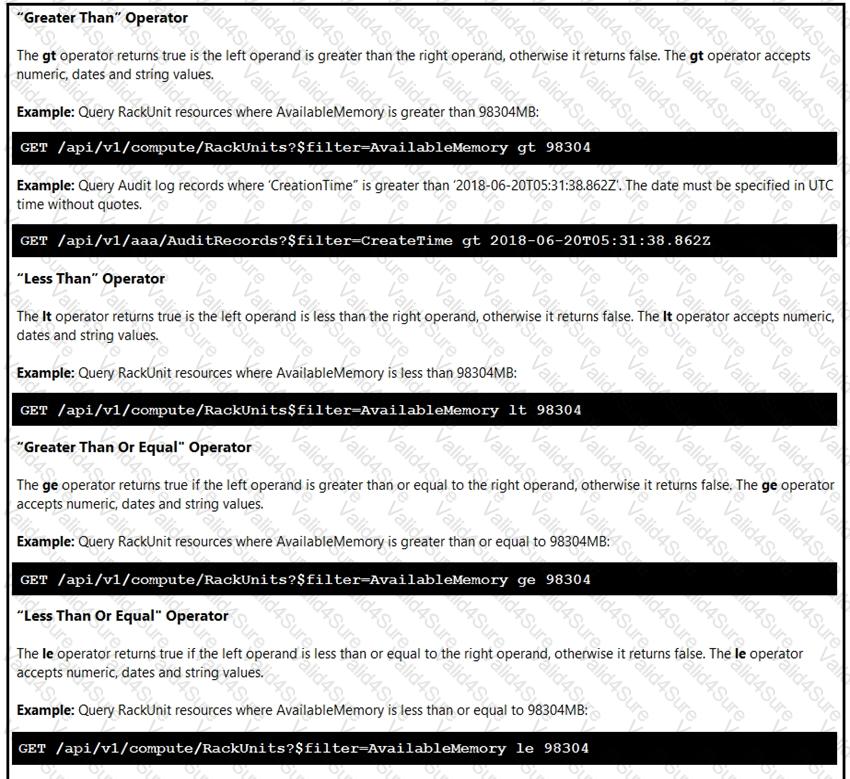
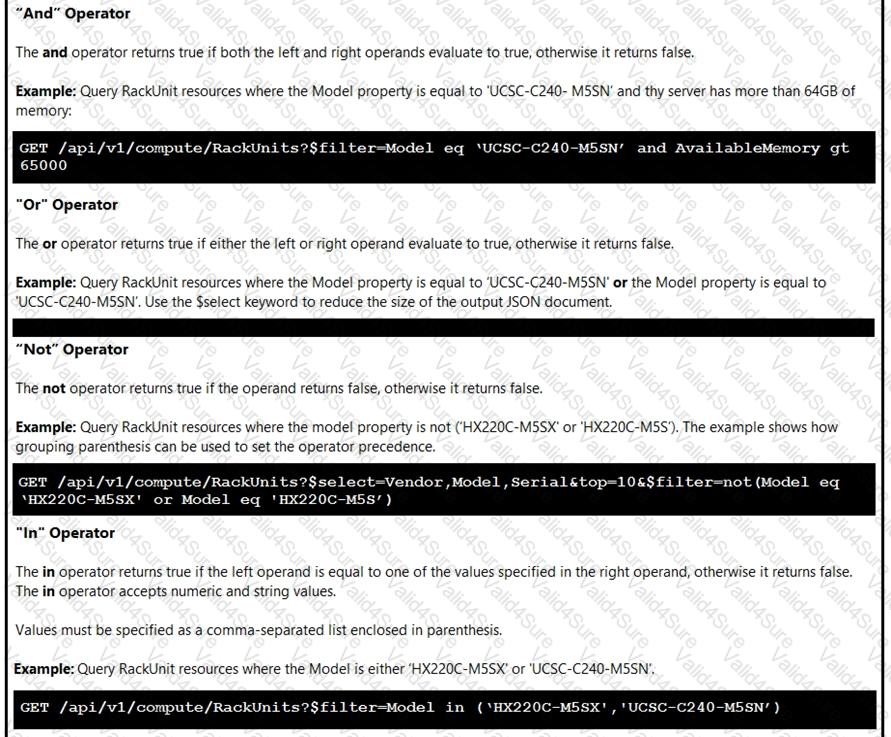

An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB.
Which REST API call accomplishes this task?
Refer to the exhibit.

An application is created to serve an enterprise Based on use and department requirements, changes are requested quarterly Which application design change improves code maintainability?
What is a consideration for using gRPC as the model-driven telemetry protocol on a Cisco IOS XE device?