350-901 Exam Dumps - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
Searching for workable clues to ace the Cisco 350-901 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 350-901 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.
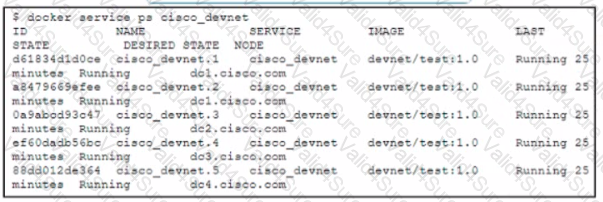
The cisco_devnet Docker swarm service runs across five replicas The development team tags and imports a new image named devnet'test 1 1 and requests that the image be upgraded on each container There must be no service outages during the upgrade process Which two design approaches must be used? (Choose two.)
A developer is deploying an application to automate the configuration and management of Osco network files and routers The application must use REST API interface lo achieve programmability. The security team mandates that the network must be protected against DDoS attacks What mitigates the attacks without impacting genuine requests?
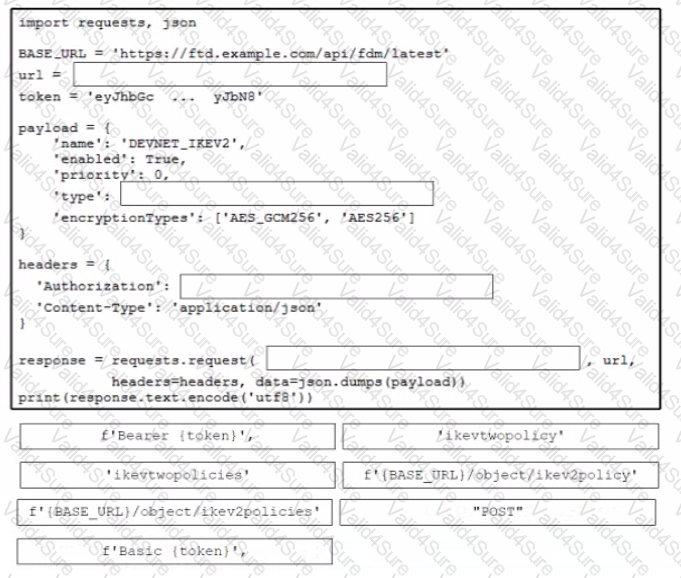
Drag and drop the code from the bottom onto the box where the code is missing to create a new IKEv2 policy Not all options are used
Refer to the exhibit.
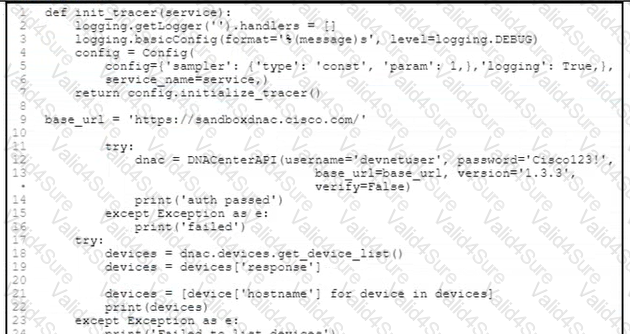
An application is created to serve the needs of an enterprise. Slow performance now impacts certain API calls, and the application design lacks observability. Which two commands improve observability and provide an output that is similar to the sample output? (Choose two.)
A)
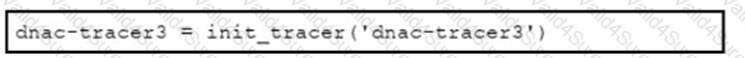
B)

C)

D)

E)
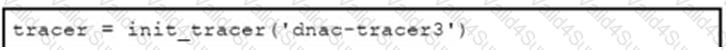
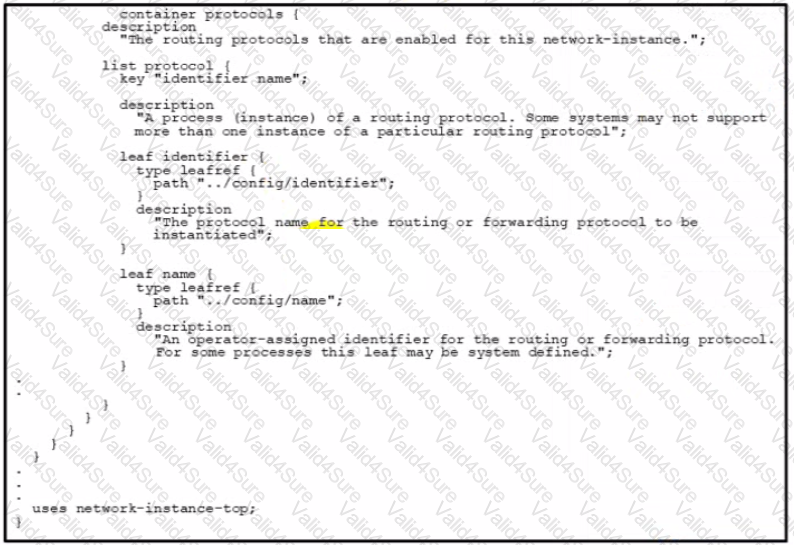
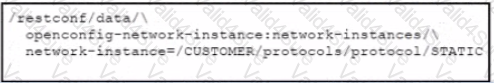
Refer to the exhibit. Which URI string retrieves configured static routes in a VRF named CUSTOMER from a RESTCONF-enabled device?
A)

B)
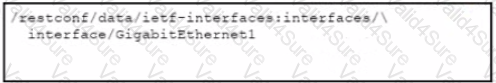
C)

D)
When end-to-end encryption is implemented, which area is most vulnerable to exploitation?
A Cisco Catalyst 9000 switch has guest shell enabled. Which Linux command installs a third-party application?
Where should distributed load balancing occur in a horizontally scalable architecture?
 C:\Users\wk\Desktop\mudassar\Untitled.png
C:\Users\wk\Desktop\mudassar\Untitled.png