312-50 Exam Dumps - Certified Ethical Hacker Exam
Searching for workable clues to ace the ECCouncil 312-50 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 312-50 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
In the software security development life cycle process, threat modeling occurs in which phase?
When creating a security program, which approach would be used if senior management is supporting and enforcing the security policy?
What is the most secure way to mitigate the theft of corporate information from a laptop that was left in a hotel room?
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed. Which security policy must the security analyst check to see if dial-out modems are allowed?
Which of the following business challenges could be solved by using a vulnerability scanner?
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
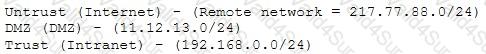
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
Which type of security document is written with specific step-by-step details?